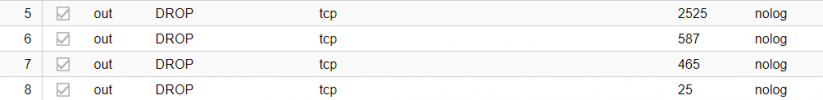
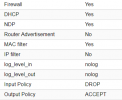
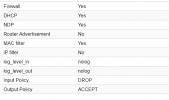
and checkbox is correctly enable on vm nic too ?
can you send the result of
#iptables-save
of your node where the vm is running ?
Here is the result of iptables and yes checkbox is enabled
-A INPUT -j PVEFW-INPUT
-A FORWARD -j PVEFW-FORWARD
-A OUTPUT -j PVEFW-OUTPUT
-A GROUP-firewallrules-IN -j MARK --set-xmark 0x0/0x80000000
-A GROUP-firewallrules-IN -p tcp -m tcp --dport 26 -j DROP
-A GROUP-firewallrules-IN -p tcp -m tcp --dport 2525 -j DROP
-A GROUP-firewallrules-IN -p tcp -m tcp --dport 443 -g PVEFW-SET-ACCEPT-MARK
-A GROUP-firewallrules-IN -p tcp -m tcp --dport 80 -g PVEFW-SET-ACCEPT-MARK
-A GROUP-firewallrules-IN -p tcp -m tcp --dport 143 -g PVEFW-SET-ACCEPT-MARK
-A GROUP-firewallrules-IN -p tcp -m tcp --dport 25 -g PVEFW-SET-ACCEPT-MARK
-A GROUP-firewallrules-IN -p tcp -m tcp --dport 143 -g PVEFW-SET-ACCEPT-MARK
-A GROUP-firewallrules-IN -p tcp -m tcp --dport 3306 -g PVEFW-SET-ACCEPT-MARK
-A GROUP-firewallrules-IN -p tcp -m tcp --dport 3389 -g PVEFW-SET-ACCEPT-MARK
-A GROUP-firewallrules-IN -m comment --comment "PVESIG:kwqVKNpG3qtPkz05K8g8Wph+jNk"
-A GROUP-firewallrules-OUT -j MARK --set-xmark 0x0/0x80000000
-A GROUP-firewallrules-OUT -p tcp -m tcp --dport 25 -j DROP
-A GROUP-firewallrules-OUT -p tcp -m tcp --dport 587 -j DROP
-A GROUP-firewallrules-OUT -p tcp -m tcp --dport 2525 -j DROP
-A GROUP-firewallrules-OUT -p tcp -m tcp --dport 465 -j DROP
-A GROUP-firewallrules-OUT -p tcp -m tcp --dport 26 -j DROP
-A GROUP-firewallrules-OUT -p tcp -m tcp --dport 25 -j DROP
-A GROUP-firewallrules-OUT -p tcp -m tcp --dport 465 -j DROP
-A GROUP-firewallrules-OUT -p tcp -m tcp --dport 587 -j DROP
-A GROUP-firewallrules-OUT -m comment --comment "PVESIG:fSxOYjCTKqR/8tW3mhpRdcAz+t4"
-A PVEFW-Drop -p tcp -m tcp --dport 43 -j PVEFW-reject
-A PVEFW-Drop -j PVEFW-DropBroadcast
-A PVEFW-HOST-OUT -p igmp -j RETURN
-A PVEFW-HOST-OUT -o vmbr0 -p tcp -m tcp --dport 25 -j DROP
-A PVEFW-HOST-OUT -o vmbr0 -p tcp -m tcp --dport 587 -j DROP
-A PVEFW-HOST-OUT -o vmbr0 -p tcp -m tcp --dport 465 -j DROP
-A PVEFW-HOST-OUT -o vmbr0 -p tcp -m tcp --dport 2525 -j DROP
-A PVEFW-HOST-OUT -o vmbr0 -p tcp -m tcp --dport 26 -j DROP
-A PVEFW-HOST-OUT -o vmbr0 -p tcp -m tcp --dport 25 -j DROP
-A PVEFW-HOST-OUT -o vmbr0 -p tcp -m tcp --dport 26 -j DROP
-A PVEFW-HOST-OUT -o vmbr0 -p tcp -m tcp --dport 2525 -j DROP
-A PVEFW-HOST-OUT -o vmbr0 -p tcp -m tcp --dport 587 -j DROP
-A PVEFW-HOST-OUT -o vmbr0 -p tcp -m tcp --dport 465 -j DROP
-A PVEFW-HOST-OUT -d 204.12.231.144/29 -p tcp -m tcp --dport 8006 -j RETURN
-A PVEFW-HOST-OUT -d 204.12.231.144/29 -p tcp -m tcp --dport 22 -j RETURN
-A PVEFW-HOST-OUT -d 204.12.231.144/29 -p tcp -m tcp --dport 5900:5999 -j RETURN
-A PVEFW-HOST-OUT -d 204.12.231.144/29 -p tcp -m tcp --dport 3128 -j RETURN
-A PVEFW-HOST-OUT -j RETURN
-A PVEFW-HOST-OUT -m comment --comment "PVESIG:fy+g+PaGXhXZAL/vwMFwAmAni+w"
-A PVEFW-INPUT -j PVEFW-HOST-IN
-A PVEFW-INPUT -m comment --comment "PVESIG:+5iMmLaxKXynOB/+5xibfx7WhFk"
-A PVEFW-OUTPUT -j PVEFW-HOST-OUT
-A PVEFW-OUTPUT -m comment --comment "PVESIG:LjHoZeSSiWAG3+2ZAyL/xuEehd0"
-A PVEFW-Reject -p tcp -m tcp --dport 43 -j PVEFW-reject
-A PVEFW-Reject -j PVEFW-DropBroadcast
-A PVEFW-Reject -p icmp -m icmp --icmp-type 3/4 -j ACCEPT
-A PVEFW-Reject -p icmp -m icmp --icmp-type 11 -j ACCEPT
-A PVEFW-Reject -m conntrack --ctstate INVALID -j DROP
-A PVEFW-Reject -p udp -m multiport --dports 135,445 -j PVEFW-reject
-A PVEFW-Reject -p udp -m udp --dport 137:139 -j PVEFW-reject
-A PVEFW-Reject -p udp -m udp --sport 137 --dport 1024:65535 -j PVEFW-reject
-A PVEFW-Reject -p tcp -m multiport --dports 135,139,445 -j PVEFW-reject
-A PVEFW-Reject -p udp -m udp --dport 1900 -j DROP
-A PVEFW-Reject -p tcp -m tcp ! --tcp-flags FIN,SYN,RST,ACK SYN -j DROP
-A PVEFW-Reject -p udp -m udp --sport 53 -j DROP
-A PVEFW-Reject -m comment --comment "PVESIG:CZJnIN6rAdpu+ej59QPr9+laMUo"
-A PVEFW-SET-ACCEPT-MARK -j MARK --set-xmark 0x80000000/0x80000000
-A PVEFW-SET-ACCEPT-MARK -m comment --comment "PVESIG:Hg/OIgIwJChBUcWU8Xnjhdd2jUY"
-A PVEFW-logflags -j DROP
-A PVEFW-logflags -m comment --comment "PVESIG:MN4PH1oPZeABMuWr64RrygPfW7A"
-A PVEFW-reject -m addrtype --dst-type BROADCAST -j DROP
-A PVEFW-reject -s 224.0.0.0/4 -j DROP
-A PVEFW-reject -p icmp -j DROP
-A PVEFW-reject -p tcp -j REJECT --reject-with tcp-reset
-A PVEFW-reject -p udp -j REJECT --reject-with icmp-port-unreachable
-A PVEFW-reject -p icmp -j REJECT --reject-with icmp-host-unreachable
-A PVEFW-reject -j REJECT --reject-with icmp-host-prohibited
-A PVEFW-reject -m comment --comment "PVESIG:Jlkrtle1mDdtxDeI9QaDSL++Npc"
-A PVEFW-smurflog -j DROP
-A PVEFW-smurflog -m comment --comment "PVESIG:2gfT1VMkfr0JL6OccRXTGXo+1qk"
-A PVEFW-smurfs -s 0.0.0.0/32 -j RETURN
-A PVEFW-smurfs -m addrtype --src-type BROADCAST -g PVEFW-smurflog
-A PVEFW-smurfs -s 224.0.0.0/4 -g PVEFW-smurflog
-A PVEFW-smurfs -m comment --comment "PVESIG:HssVe5QCBXd5mc9kC88749+7fag"
-A PVEFW-tcpflags -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,PSH,URG -g PVEFW-logflags
-A PVEFW-tcpflags -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG NONE -g PVEFW-logflags
-A PVEFW-tcpflags -p tcp -m tcp --tcp-flags SYN,RST SYN,RST -g PVEFW-logflags
-A PVEFW-tcpflags -p tcp -m tcp --tcp-flags FIN,SYN FIN,SYN -g PVEFW-logflags
-A PVEFW-tcpflags -p tcp -m tcp --sport 0 --tcp-flags FIN,SYN,RST,ACK SYN -g PVEFW-logflags
-A PVEFW-tcpflags -m comment --comment "PVESIG:CMFojwNPqllyqD67NeI5m+bP5mo"
-A tap1001i0-IN -p udp -m udp --sport 67 --dport 68 -j ACCEPT
-A tap1001i0-IN -j GROUP-firewallrules-IN
-A tap1001i0-IN -m mark --mark 0x80000000/0x80000000 -j ACCEPT
-A tap1001i0-IN -j PVEFW-Drop
-A tap1001i0-IN -j DROP
-A tap1001i0-IN -m comment --comment "PVESIG:SPrJ+kO2JLex7wVrvhbYT3P08F4"
-A tap1001i0-OUT -p udp -m udp --sport 68 --dport 67 -g PVEFW-SET-ACCEPT-MARK
-A tap1001i0-OUT -m mac ! --mac-source 00:16:3E:6F:44:B3 -j DROP
-A tap1001i0-OUT -j MARK --set-xmark 0x0/0x80000000
-A tap1001i0-OUT -j GROUP-firewallrules-OUT
-A tap1001i0-OUT -m mark --mark 0x80000000/0x80000000 -j RETURN
-A tap1001i0-OUT -g PVEFW-SET-ACCEPT-MARK
-A tap1001i0-OUT -m comment --comment "PVESIG:YNssiiXqnQAUarj4vjL3n7OnKjU"
-A tap1002i0-IN -p udp -m udp --sport 67 --dport 68 -j ACCEPT
-A tap1002i0-IN -j GROUP-firewallrules-IN
-A tap1002i0-IN -m mark --mark 0x80000000/0x80000000 -j ACCEPT
-A tap1002i0-IN -j PVEFW-Drop
-A tap1002i0-IN -j DROP
-A tap1002i0-IN -m comment --comment "PVESIG:EySKt5yYABnPxUPRAr7GeTF5W0w"
-A tap1002i0-OUT -p udp -m udp --sport 68 --dport 67 -g PVEFW-SET-ACCEPT-MARK
-A tap1002i0-OUT -m mac ! --mac-source 00:16:3E:9F:8C:66 -j DROP
-A tap1002i0-OUT -j MARK --set-xmark 0x0/0x80000000
-A tap1002i0-OUT -j GROUP-firewallrules-OUT
-A tap1002i0-OUT -m mark --mark 0x80000000/0x80000000 -j RETURN
-A tap1002i0-OUT -g PVEFW-SET-ACCEPT-MARK
-A tap1002i0-OUT -m comment --comment "PVESIG:0GJiLe4u6mmWVzOK3DYNvMTXu5Q"
-A tap1004i0-IN -p udp -m udp --sport 67 --dport 68 -j ACCEPT
-A tap1004i0-IN -j GROUP-firewallrules-IN
-A tap1004i0-IN -m mark --mark 0x80000000/0x80000000 -j ACCEPT
-A tap1004i0-IN -j PVEFW-Drop
-A tap1004i0-IN -j DROP
-A tap1004i0-IN -m comment --comment "PVESIG:nbp4nLO2eAANLYLSolafNLEJonY"
-A tap1004i0-OUT -p udp -m udp --sport 68 --dport 67 -g PVEFW-SET-ACCEPT-MARK
-A tap1004i0-OUT -m mac ! --mac-source 00:16:3E:34:94:6C -j DROP
-A tap1004i0-OUT -j MARK --set-xmark 0x0/0x80000000
-A tap1004i0-OUT -j GROUP-firewallrules-OUT
-A tap1004i0-OUT -m mark --mark 0x80000000/0x80000000 -j RETURN
-A tap1004i0-OUT -g PVEFW-SET-ACCEPT-MARK
-A tap1004i0-OUT -m comment --comment "PVESIG:AcOe6zv8l9rk6jMcxEheokcssc8"
-A tap1005i0-IN -p udp -m udp --sport 67 --dport 68 -j ACCEPT
-A tap1005i0-IN -j GROUP-firewallrules-IN
-A tap1005i0-IN -m mark --mark 0x80000000/0x80000000 -j ACCEPT
-A tap1005i0-IN -j PVEFW-Drop
-A tap1005i0-IN -j DROP
-A tap1005i0-IN -m comment --comment "PVESIG:xDdBz6Ogxk0GvymTH6gBuJJJpK0"
-A tap1005i0-OUT -p udp -m udp --sport 68 --dport 67 -g PVEFW-SET-ACCEPT-MARK
-A tap1005i0-OUT -m mac ! --mac-source 00:16:3E:90:1E:13 -j DROP
-A tap1005i0-OUT -j MARK --set-xmark 0x0/0x80000000
-A tap1005i0-OUT -j GROUP-firewallrules-OUT
-A tap1005i0-OUT -m mark --mark 0x80000000/0x80000000 -j RETURN
-A tap1005i0-OUT -g PVEFW-SET-ACCEPT-MARK
-A tap1005i0-OUT -m comment --comment "PVESIG:E9+I79LeNsB+zOTMh2UFgA6B0U0"
-A tap1006i0-IN -p udp -m udp --sport 67 --dport 68 -j ACCEPT
-A tap1006i0-IN -j GROUP-firewallrules-IN
-A tap1006i0-IN -m mark --mark 0x80000000/0x80000000 -j ACCEPT
-A tap1006i0-IN -j PVEFW-Drop
-A tap1006i0-IN -j DROP
-A tap1006i0-IN -m comment --comment "PVESIG:+XBfu1j/L9PZxQnh5s6AvU6dEoE"
-A tap1006i0-OUT -p udp -m udp --sport 68 --dport 67 -g PVEFW-SET-ACCEPT-MARK
-A tap1006i0-OUT -m mac ! --mac-source 00:16:3E:F4:86:58 -j DROP
-A tap1006i0-OUT -j MARK --set-xmark 0x0/0x80000000
-A tap1006i0-OUT -j GROUP-firewallrules-OUT
-A tap1006i0-OUT -m mark --mark 0x80000000/0x80000000 -j RETURN
-A tap1006i0-OUT -g PVEFW-SET-ACCEPT-MARK
-A tap1006i0-OUT -m comment --comment "PVESIG:1NOG8Cg80sSzULHNwAEdEOlqVOU"
-A tap1007i0-IN -p udp -m udp --sport 67 --dport 68 -j ACCEPT
-A tap1007i0-IN -j GROUP-firewallrules-IN
-A tap1007i0-IN -m mark --mark 0x80000000/0x80000000 -j ACCEPT
-A tap1007i0-IN -j PVEFW-Drop
-A tap1007i0-IN -j DROP
-A tap1007i0-IN -m comment --comment "PVESIG:c46gy5dVTocK32L0ps9+X/7zvVY"
-A tap1007i0-OUT -p udp -m udp --sport 68 --dport 67 -g PVEFW-SET-ACCEPT-MARK
-A tap1007i0-OUT -m mac ! --mac-source 00:16:3E:C5:AC:6B -j DROP
-A tap1007i0-OUT -j MARK --set-xmark 0x0/0x80000000
-A tap1007i0-OUT -j GROUP-firewallrules-OUT
-A tap1007i0-OUT -m mark --mark 0x80000000/0x80000000 -j RETURN
-A tap1007i0-OUT -g PVEFW-SET-ACCEPT-MARK
-A tap1007i0-OUT -m comment --comment "PVESIG:i4bkTPof3gYX1R9DnJeZXT2Uyug"
-A tap1008i0-IN -p udp -m udp --sport 67 --dport 68 -j ACCEPT
-A tap1008i0-IN -j GROUP-firewallrules-IN
-A tap1008i0-IN -m mark --mark 0x80000000/0x80000000 -j ACCEPT
-A tap1008i0-IN -j PVEFW-Drop
-A tap1008i0-IN -j DROP
-A tap1008i0-IN -m comment --comment "PVESIG:mXgPTLnFCN0C2KXKaHOarBf/ZO4"
-A tap1008i0-OUT -p udp -m udp --sport 68 --dport 67 -g PVEFW-SET-ACCEPT-MARK
-A tap1008i0-OUT -m mac ! --mac-source 00:16:3E:07:34:A9 -j DROP
-A tap1008i0-OUT -j MARK --set-xmark 0x0/0x80000000
-A tap1008i0-OUT -j GROUP-firewallrules-OUT
-A tap1008i0-OUT -m mark --mark 0x80000000/0x80000000 -j RETURN
-A tap1008i0-OUT -g PVEFW-SET-ACCEPT-MARK
-A tap1008i0-OUT -m comment --comment "PVESIG:NFSAGdEpT+STBgeLs+hVrW1Lwyc"
-A tap1009i0-IN -p udp -m udp --sport 67 --dport 68 -j ACCEPT
-A tap1009i0-IN -j GROUP-firewallrules-IN
-A tap1009i0-IN -m mark --mark 0x80000000/0x80000000 -j ACCEPT
-A tap1009i0-IN -j PVEFW-Drop
-A tap1009i0-IN -j DROP
-A tap1009i0-IN -m comment --comment "PVESIG:HGhGkIE3Uvw8m4U7Y6oR1+/TKNQ"
-A tap1009i0-OUT -p udp -m udp --sport 68 --dport 67 -g PVEFW-SET-ACCEPT-MARK
-A tap1009i0-OUT -m mac ! --mac-source 00:16:3E:18

2:9D -j DROP
-A tap1009i0-OUT -j MARK --set-xmark 0x0/0x80000000
-A tap1009i0-OUT -j GROUP-firewallrules-OUT
-A tap1009i0-OUT -m mark --mark 0x80000000/0x80000000 -j RETURN
-A tap1009i0-OUT -g PVEFW-SET-ACCEPT-MARK
-A tap1009i0-OUT -m comment --comment "PVESIG:MDgUUBY8E7LrYUibIFZd0IxmZu8"
-A tap104i0-IN -p udp -m udp --sport 67 --dport 68 -j ACCEPT
-A tap104i0-IN -j GROUP-firewallrules-IN
-A tap104i0-IN -m mark --mark 0x80000000/0x80000000 -j ACCEPT
-A tap104i0-IN -j PVEFW-Drop
-A tap104i0-IN -j DROP
-A tap104i0-IN -m comment --comment "PVESIG:x+CS9zC7RD0WVKk7mnk19ioe9no"
-A tap104i0-OUT -p udp -m udp --sport 68 --dport 67 -g PVEFW-SET-ACCEPT-MARK
-A tap104i0-OUT -m mac ! --mac-source 7A:FD:3D:7E:F7:46 -j DROP
-A tap104i0-OUT -j MARK --set-xmark 0x0/0x80000000
-A tap104i0-OUT -j GROUP-firewallrules-OUT
-A tap104i0-OUT -m mark --mark 0x80000000/0x80000000 -j RETURN
-A tap104i0-OUT -g PVEFW-SET-ACCEPT-MARK
-A tap104i0-OUT -m comment --comment "PVESIG:sXQHPAP7VHhggrAXuL/uKa1KtyM"
-A tap105i0-IN -p udp -m udp --sport 67 --dport 68 -j ACCEPT
-A tap105i0-IN -j GROUP-firewallrules-IN
-A tap105i0-IN -m mark --mark 0x80000000/0x80000000 -j ACCEPT
-A tap105i0-IN -j PVEFW-Drop
-A tap105i0-IN -j DROP
-A tap105i0-IN -m comment --comment "PVESIG:FquqH8f+NeqZW9wkZRADofSazHI"
-A tap105i0-OUT -p udp -m udp --sport 68 --dport 67 -g PVEFW-SET-ACCEPT-MARK
-A tap105i0-OUT -m mac ! --mac-source F6:1E:71:4F:8D:C8 -j DROP
-A tap105i0-OUT -j MARK --set-xmark 0x0/0x80000000
-A tap105i0-OUT -j GROUP-firewallrules-OUT
-A tap105i0-OUT -m mark --mark 0x80000000/0x80000000 -j RETURN
-A tap105i0-OUT -g PVEFW-SET-ACCEPT-MARK
-A tap105i0-OUT -m comment --comment "PVESIG:rIYbKsLTPHgU1c3RA0JfYVDn/Fk"
-A tap112i0-IN -p udp -m udp --sport 67 --dport 68 -j ACCEPT
-A tap112i0-IN -j GROUP-firewallrules-IN
-A tap112i0-IN -m mark --mark 0x80000000/0x80000000 -j ACCEPT
-A tap112i0-IN -j PVEFW-Drop
-A tap112i0-IN -j DROP
-A tap112i0-IN -m comment --comment "PVESIG:cCJ6uZu0XBnJqTSy66tfO1Zyarw"
-A tap112i0-OUT -p udp -m udp --sport 68 --dport 67 -g PVEFW-SET-ACCEPT-MARK
-A tap112i0-OUT -m mac ! --mac-source 66:AD:3F

3:E0:3C -j DROP
-A tap112i0-OUT -j MARK --set-xmark 0x0/0x80000000
-A tap112i0-OUT -j GROUP-firewallrules-OUT
-A tap112i0-OUT -m mark --mark 0x80000000/0x80000000 -j RETURN
-A tap112i0-OUT -g PVEFW-SET-ACCEPT-MARK
-A tap112i0-OUT -m comment --comment "PVESIG:lWvLZAtsyEGBE3zgu/QqlUNGAsE"
COMMIT