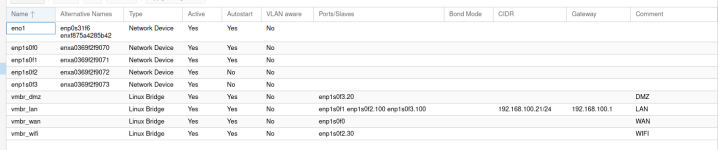
I did this with pfSense, not OPNsense, but the differences should be immaterial. My hardware set up is an ASrock Industrial IMB-V2000M motherboard, with two built in Realtek NICs and an Intel X520 dual port SFP+ 10gbe NIC. The first step was to get the Realtek NICs operational, which may not apply to you. I used the the actual official Realtek Linux drivers and installed them using DKMS. Once I had all four NICs working, I assigned vmbr0 to one of the X520 ports. Note, I could have used any of the 4 NICs but I wanted a 10GBE connection to my 10gbe managed switch, and I decided to dedicate the two Realtek NICs to my redundant WAN ports (I have two internet providers, Xfinity and T-Mobile). Anyway, vmbr0 was assinged to a nic and I created two virtual NICs of of that: vmbro.100 and vmbr0.3. I assigned static IPs to both of these. VLAN 100 is my management VLAN and the proxmox web UI is on this IP address. VLAN 3 is my non-routed storage VLAN that connects all my proxmox nodes to my NAS, without having to leave the switch/be routed by pfSense. I also created vmbr1, vmbr2, and vmbr3. Each were assigned to one of the other NICs. Inside my pfSense VM, I added three virtual NICs, one assigned to vmbr0 which becomes the LAN port in pfSense, one assigned to vmbr1 which becomes the WAN port in pfSense, and one assigned to vmbr2, which is initially assigned to OPT1 in pfSense and later renamed/reassigned to WAN2.
the remaining bridge, vmbr3, is assigned a static IP that doesn't correspond to the IP ranges of any of my VLANs or anything else for that matter. It is the port I use to log into pfSense to manage everything in Proxmox should pfSense go down or need to be restored from backup. I have it set to 192.168.99.99 To use that port, I manually set the IP on my laptop to 192.168.99.100/255.255.0.0 and just plug then in direct, no switch or anything else in between. You will use this port initially to set up the pfsense VM and get pfsense (or OPNsense) installed. I used vmbr1 for the initial pfSense install, then I shut down the VM and added all the other virtual NICs. From the command line (Proxmox VM Spice console) I had to reassign the interfaces. After that I can log in from my normal network and go through the rest of the cofiguration.
Note that my setup is complicated because I am running my Proxmox gui on a VLAN that needed to be defined within pfSense. If you go the same route, you need to have a means of logging into Proxmox before pfSense is up and running. If you don't have enough NICs, you could maybe use something like a USB NIC.
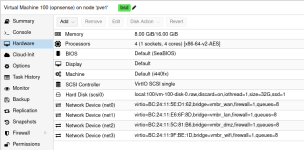
For the pfSense VM I used OVMF (UEFI) as the bios, q35 as the machine type, Virtio SCSI single for the drive, and Virtio (paravirtualized) for my virtual network interfaces. I made sure firewall was unchecked and no vlan was noted in the VLAN field (leave it blank). I gave my VM 6 cores (just because this motherboard has 8 cores/16 threads total, and I have plenty to spare) and 4gb of memory, non ballooning.