Hey,
I am successfully using the OpenID Connect Server to authenticate with my PVE Cluster.
The configuration I currently have:
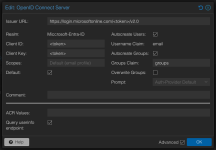
That works like a charm, and I am able to use SSO to sign in.
But:
It does not sync any groups, so if somebody logs in for the first time, they have no permission have to be added to a group manually.
Instead, I would prefer to have Groups/Roles in Azure autocreated in Proxmox on login.
My assumption is, that either the Groups Claim is wrong, or I need some more scopes defined in Azure.
Does anyone have the group sync working with EntraID and can tell me, what scopes I need to assign in Azure and what "Groups Claim" value I have to define?
I already checked those pages, but without success:
- https://bugzilla.proxmox.com/show_bug.cgi?id=4411
- https://forum.proxmox.com/threads/openid-connect-default-group.103394/#post-445387
- https://pve.proxmox.com/pve-docs/chapter-pveum.html#pveum_openid
I am successfully using the OpenID Connect Server to authenticate with my PVE Cluster.
The configuration I currently have:

That works like a charm, and I am able to use SSO to sign in.
But:
It does not sync any groups, so if somebody logs in for the first time, they have no permission have to be added to a group manually.
Instead, I would prefer to have Groups/Roles in Azure autocreated in Proxmox on login.
My assumption is, that either the Groups Claim is wrong, or I need some more scopes defined in Azure.
Does anyone have the group sync working with EntraID and can tell me, what scopes I need to assign in Azure and what "Groups Claim" value I have to define?
I already checked those pages, but without success:
- https://bugzilla.proxmox.com/show_bug.cgi?id=4411
- https://forum.proxmox.com/threads/openid-connect-default-group.103394/#post-445387
- https://pve.proxmox.com/pve-docs/chapter-pveum.html#pveum_openid

