Hi!
This is a description of a solution that I'm using in my home lab. Maybe this solution can help other Proxmox users.
I'm using Proxmox for a while. I've created a 3 servers cluster. Despite the fact that every web interface of those servers provides the same information, I didn't have a single IP as unified entrance point. With this scenario, I decided to implement a keepalived load balancer between my servers in these clusters and create a VIP to create a single point to access the cluster.
If you don't know keepalived, this is a simple solution, available via apt from standard repository, that implements a VIP – Virtual IP – between some group of servers. You must define a master node, that will receive requests redirected from the VIP, and backup nodes, that will assume the master function if the master is offline.
For others that like this idea, the process is pretty simple. You probably will spend something between 15 and 30 minutes to implement everything.
Maybe this feature can be part of some next version of Proxmox. I would love to see a native VIP setting at the Datacenter level.
How to:
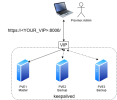
The steps 1-3 must be done for all PVE servers.
1 – Install keepalived in your servers
2 – Create and edit a keepalived.conf
Add the following content to this file, replacing:
#STATE# -> must be MASTER or BACKUP
#INTERFACE# -> interface name used to the cluster, probably vmbr0
#MYIP# -> PVE IP address
#SERVERSIPS# -> other PVE servers IPs. One IP per line.
#PASSWD# -> an 8 char password that keepalived will be used to authenticate. Must be the same for all PVE servers.
#VIP#/#CIR# -> your VIP. Be sure that this IP is free to use as a static IP in your network.
Save and close the file (ctr+x -> y).
3 – Restart keepalived
4 – Test your VIP address
Open your browser and try to access https://<YOUR_VIP>:8006/
If you have access granted to Proxmox WI, your VIP is working fine in your master node.
Now, on PVE Master node
Refresh https://<YOUR_VIP>:8006/
At this situation, one of the backup nodes must handle the VIP and you must have access to Proxmox WI.
At PVE Master
This is a description of a solution that I'm using in my home lab. Maybe this solution can help other Proxmox users.
I'm using Proxmox for a while. I've created a 3 servers cluster. Despite the fact that every web interface of those servers provides the same information, I didn't have a single IP as unified entrance point. With this scenario, I decided to implement a keepalived load balancer between my servers in these clusters and create a VIP to create a single point to access the cluster.
If you don't know keepalived, this is a simple solution, available via apt from standard repository, that implements a VIP – Virtual IP – between some group of servers. You must define a master node, that will receive requests redirected from the VIP, and backup nodes, that will assume the master function if the master is offline.
For others that like this idea, the process is pretty simple. You probably will spend something between 15 and 30 minutes to implement everything.
Maybe this feature can be part of some next version of Proxmox. I would love to see a native VIP setting at the Datacenter level.
How to:

The steps 1-3 must be done for all PVE servers.
1 – Install keepalived in your servers
# apt install keepalived2 – Create and edit a keepalived.conf
# nano /etc/keepalived/keepalived.confAdd the following content to this file, replacing:
#STATE# -> must be MASTER or BACKUP
#INTERFACE# -> interface name used to the cluster, probably vmbr0
#MYIP# -> PVE IP address
#SERVERSIPS# -> other PVE servers IPs. One IP per line.
#PASSWD# -> an 8 char password that keepalived will be used to authenticate. Must be the same for all PVE servers.
#VIP#/#CIR# -> your VIP. Be sure that this IP is free to use as a static IP in your network.
Code:
vrrp_instance VI_1 {
state #STATE#
interface #INTERFACE#
virtual_router_id 55
priority #PRIORITY#
advert_int 1
unicast_src_ip #MYIP#
unicast_peer {
#SERVERSIPS#
}
authentication {
auth_type PASS
auth_pass #PASSWD#
}
virtual_ipaddress {
#VIP#/#CIR#
}
}Save and close the file (ctr+x -> y).
3 – Restart keepalived
# service keepalived restart4 – Test your VIP address
Open your browser and try to access https://<YOUR_VIP>:8006/
If you have access granted to Proxmox WI, your VIP is working fine in your master node.
Now, on PVE Master node
# service keepalived stopRefresh https://<YOUR_VIP>:8006/
At this situation, one of the backup nodes must handle the VIP and you must have access to Proxmox WI.
At PVE Master
# service keepalived start
Last edited: