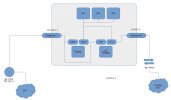
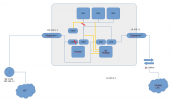
Should work. Your em0 + vmbr0 is then your WAN side and em1 + vmbr1 your LAN side .
But I would add a third DMZ subnet for more security. You don't need a third NIC or a VLAN capable switch for that as long as you don't want to add other physical host to your DMZ. Its isn't good to run your sevices inside your LAN, especially if you want them to be accessible from the internet (creating port-forwards to the VMs). Lets say one of your webservers inside a VM got a open vulnerability and a bot sees this and hacks your VM. If that VM is part of your LAN the attacker now has access to all other of your private computers, maybe a NAS with private data and so on. So its better to have the VMs in a dedicated subnet where you setup your pfsenses firewall rules in a way that everything inside the DMZ subnet can access the WAN subnet (and so the internet) but not the LAN subnet. But the LAN subnet can still access the DMZ subnet, so your hosts in the LAN can access all services your host with your VMs. If then a VM gets hacked its isolated in the DMZ subnet and the attacker wont be able to access your other computers in the LAN subnet.
For the DMZ subnet I would use vmbr0 with no IP or gateway set and not connected to any physical NIC, so just connected to your pfsense and all your other VMs using a virtual NIC. Your VMs can then have the IP of the pfsenses DMZ virtual NIC as the gateway and the pfsense will route the traffic from the DMZ to the WAN. I really would prefer vmbr0 for the DMZ because vmbr0 is what Proxmox VE (PVE) will choose by default when creating you VMs. That way it is less likely that you by accident add a VM to the LAN or even worse WAN bridge.
Then you got two options:
1.) Put your PVE on the WAN side with your physical router as the gateway and set a IP of WAN subnet. Benefit would be that your PVE server can still go online to download upgrades if your pfsense VM isn't running. Can be useful for example if a PVE upgrade will break the pfsense VM so it won't be able to start anymore but then your whole server will be offline too so you can't fix that.
Disadvantage would be that you won't be able to use 'exposed host' or your physical router just as a modem because then the WAN side of your PVE server would be completely unprotected and everyone in the world could attack your servers management ports. And you would need to add additional firewall rules in your pfsense so that VMs the DMZ can't access your PVEs management IP.
2.) Second option would be to set your pfsenses LAN IP as your gateway and to give the PVE server a IP of your LANs subnet range. That way the servers managent is on the more secure LAN side and protedted by the pfsense firewall. Its also easier to manage your server because its IP is part of your LAN subnet so you can even access the PVE webUI if your pfsense VM isn't running without needing to attach a physical client like a laptop to your WAN subnet.
Downside is that PVE won't be able to go online in case the pfsense VM isn't running.
I personally would go with option 2, which would be something like this:
For your LAN I would use vmbr1 and set a IP of your LAN subnet range and set the pfsenses LAN IP as the gateway. That way your PVEs webUI + SSH will only be available from the LAN subnet
Attach vmbr1 to em1 and create a virtual NIC for your pfsense also attached to vmbr1.
For the WAN subnet I would create vmbr2, attach it to em0 and don't set a IP or gateway. Also attach a virtual NIC of your pfsense VM to that vmbr2.
You might consider setting your pfsenses WAN IP as the 'exposed host' (thats basically like a port-forward of all ports from the public IP to the IP of your exposed host...so that host is completely esposed to the internet) in your physical routers webUI or even deativate the router/firewall functions of your physical router completely to use it just as a modem where your pfsense then could establich the internet connection using PPPoE.
Benefit in both cases is that you don't need to do everything twice (like port forwards) and only need to care about the pfsense firewall.
And you might want to buy a Wifi AP and connect it to your switch as everything connected to your physical routers Wifi will be part of the less secure (or even unsecure) WAN subnet.