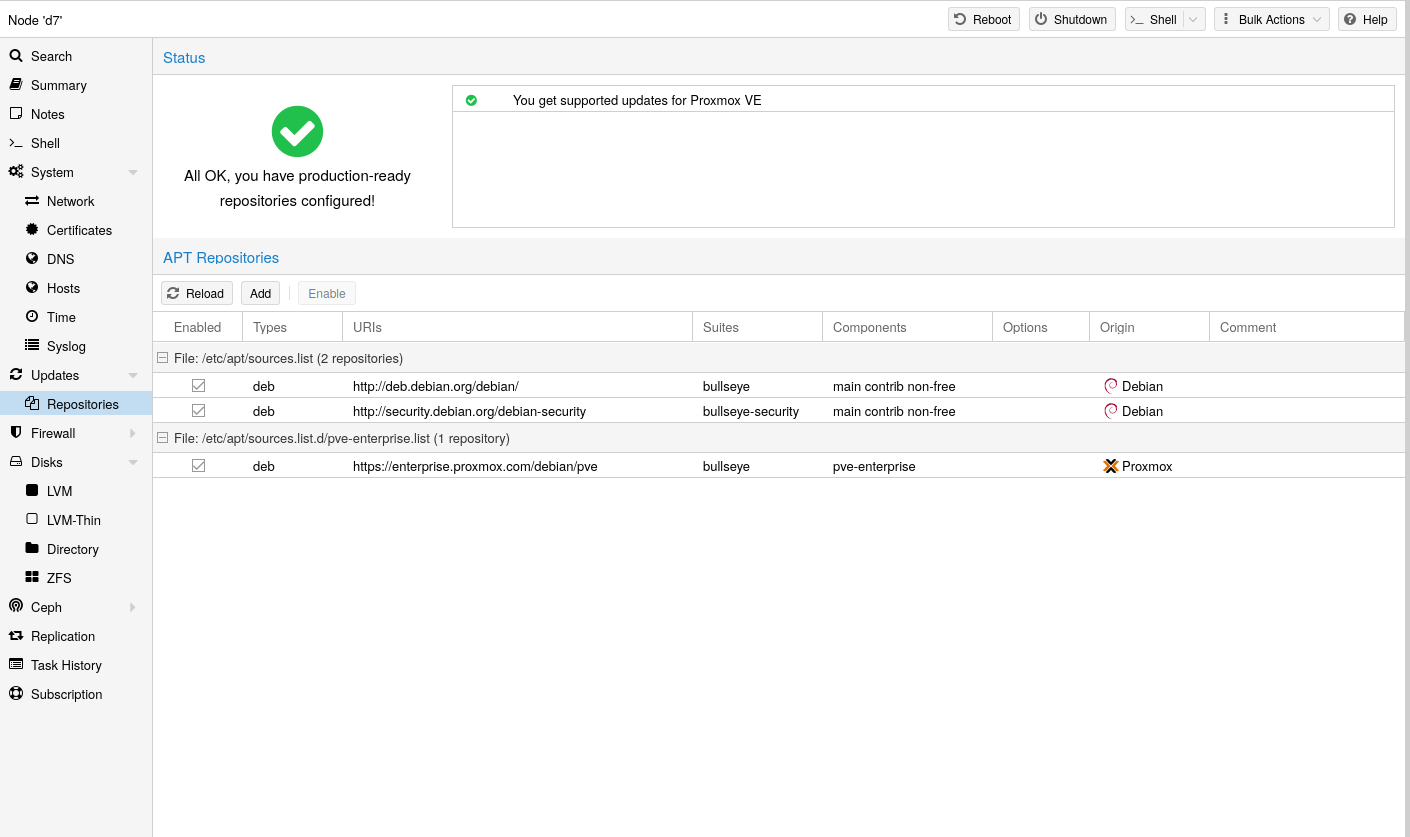
Still no chance I'm afraid:
root@proxmox:~# apt update
Hit:1
http://ftp.fr.debian.org/debian bullseye InRelease
Hit:2
http://security.debian.org bullseye-security InRelease
Hit:3
http://ftp.fr.debian.org/debian bullseye-updates InRelease
Err:4
https://enterprise.proxmox.com/debian/pve bullseye InRelease
401 Unauthorized [IP: 51.91.38.34 443]
Reading package lists... Done
E: Failed to fetch
https://enterprise.proxmox.com/debian/pve/dists/bullseye/InRelease 401 Unauthorized [IP: 51.91.38.34 443]
E: The repository '
https://enterprise.proxmox.com/debian/pve bullseye InRelease' is not signed.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
root@proxmox:~# apt update && apt full-upgrade
Hit:1
http://security.debian.org bullseye-security InRelease
Hit:2
http://ftp.fr.debian.org/debian bullseye InRelease
Hit:3
http://ftp.fr.debian.org/debian bullseye-updates InRelease
Err:4
https://enterprise.proxmox.com/debian/pve bullseye InRelease
401 Unauthorized [IP: 51.91.38.34 443]
Reading package lists... Done
E: Failed to fetch
https://enterprise.proxmox.com/debian/pve/dists/bullseye/InRelease 401 Unauthorized [IP: 51.91.38.34 443]
E: The repository '
https://enterprise.proxmox.com/debian/pve bullseye InRelease' is not signed.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.