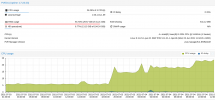
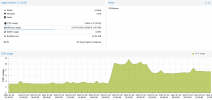
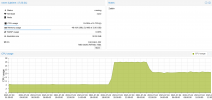
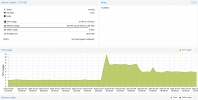
Jul 3 11:02:49 kvm1 systemd[1]: getty@tty1.service: Current command vanished from the unit file, execution of the command list won't be resumed.
Jul 3 11:02:49 kvm1 systemd[1]: Mounting /mnt/pve/cephfs...
Jul 3 11:02:49 kvm1 kernel: [ 122.285192] libceph: mon1 (1)10.0.0.2:6789 session established
Jul 3 11:02:49 kvm1 mount[3470]: mount error: no mds server is up or the cluster is laggy
Jul 3 11:02:49 kvm1 systemd[1]: mnt-pve-cephfs.mount: Mount process exited, code=exited, status=32/n/a
Jul 3 11:02:49 kvm1 systemd[1]: mnt-pve-cephfs.mount: Failed with result 'exit-code'.
Jul 3 11:02:49 kvm1 systemd[1]: Failed to mount /mnt/pve/cephfs.
Jul 3 11:02:49 kvm1 kernel: [ 122.286555] libceph: client82474213 fsid c2f2d56b-77d3-4c42-bbba-748d86cc2e2a
Jul 3 11:02:49 kvm1 kernel: [ 122.286611] ceph: No mds server is up or the cluster is laggy
Jul 3 11:02:49 kvm1 pvestatd[2195]: mount error: See "systemctl status mnt-pve-cephfs.mount" and "journalctl -xe" for details.
Jul 3 11:02:58 kvm1 systemd[1]: Reloading.
Jul 3 11:02:59 kvm1 systemd[1]: Mounting /mnt/pve/cephfs...
Jul 3 11:02:59 kvm1 mount[3627]: mount error: no mds server is up or the cluster is laggy
Jul 3 11:02:59 kvm1 systemd[1]: mnt-pve-cephfs.mount: Mount process exited, code=exited, status=32/n/a
Jul 3 11:02:59 kvm1 systemd[1]: mnt-pve-cephfs.mount: Failed with result 'exit-code'.
Jul 3 11:02:59 kvm1 systemd[1]: Failed to mount /mnt/pve/cephfs.
Jul 3 11:02:59 kvm1 kernel: [ 132.210068] libceph: mon0 (1)10.0.0.1:6789 session established
Jul 3 11:02:59 kvm1 kernel: [ 132.210475] libceph: client82474234 fsid c2f2d56b-77d3-4c42-bbba-748d86cc2e2a
Jul 3 11:02:59 kvm1 kernel: [ 132.210554] ceph: No mds server is up or the cluster is laggy
Jul 3 11:02:59 kvm1 pvestatd[2195]: mount error: See "systemctl status mnt-pve-cephfs.mount" and "journalctl -xe" for details.
Jul 3 11:03:00 kvm1 systemd[1]: Starting Proxmox VE replication runner...
Jul 3 11:03:01 kvm1 systemd[1]: pvesr.service: Succeeded.
Jul 3 11:03:01 kvm1 systemd[1]: Started Proxmox VE replication runner.
Jul 3 11:03:05 kvm1 systemd[1]: Started Session 4 of user admin.
Jul 3 11:03:08 kvm1 systemd[1]: Reloading.
Jul 3 11:03:09 kvm1 systemd[1]: Mounting /mnt/pve/cephfs...
Jul 3 11:03:09 kvm1 mount[3785]: mount error: no mds server is up or the cluster is laggy
Jul 3 11:03:09 kvm1 kernel: [ 142.320536] libceph: mon1 (1)10.0.0.2:6789 session established
Jul 3 11:03:09 kvm1 kernel: [ 142.321296] libceph: client82474243 fsid c2f2d56b-77d3-4c42-bbba-748d86cc2e2a
Jul 3 11:03:09 kvm1 kernel: [ 142.321347] ceph: No mds server is up or the cluster is laggy
Jul 3 11:03:09 kvm1 systemd[1]: mnt-pve-cephfs.mount: Mount process exited, code=exited, status=32/n/a
Jul 3 11:03:09 kvm1 systemd[1]: mnt-pve-cephfs.mount: Failed with result 'exit-code'.
Jul 3 11:03:09 kvm1 systemd[1]: Failed to mount /mnt/pve/cephfs.
Jul 3 11:03:09 kvm1 pvestatd[2195]: mount error: See "systemctl status mnt-pve-cephfs.mount" and "journalctl -xe" for details.
Jul 3 11:03:18 kvm1 systemd[1]: Reloading.
Jul 3 11:03:19 kvm1 systemd[1]: Mounting /mnt/pve/cephfs...
Jul 3 11:03:19 kvm1 kernel: [ 152.224645] libceph: mon0 (1)10.0.0.1:6789 session established
Jul 3 11:03:19 kvm1 kernel: [ 152.224966] libceph: client82474260 fsid c2f2d56b-77d3-4c42-bbba-748d86cc2e2a
Jul 3 11:03:19 kvm1 kernel: [ 152.225030] ceph: No mds server is up or the cluster is laggy
Jul 3 11:03:19 kvm1 mount[3955]: mount error: no mds server is up or the cluster is laggy
Jul 3 11:03:19 kvm1 systemd[1]: mnt-pve-cephfs.mount: Mount process exited, code=exited, status=32/n/a
Jul 3 11:03:19 kvm1 systemd[1]: mnt-pve-cephfs.mount: Failed with result 'exit-code'.
Jul 3 11:03:19 kvm1 systemd[1]: Failed to mount /mnt/pve/cephfs.
Jul 3 11:03:19 kvm1 pvestatd[2195]: mount error: See "systemctl status mnt-pve-cephfs.mount" and "journalctl -xe" for details.
Jul 3 11:03:29 kvm1 systemd[1]: Reloading.
Jul 3 11:03:29 kvm1 systemd[1]: Mounting /mnt/pve/cephfs...
Jul 3 11:03:29 kvm1 kernel: [ 162.288591] libceph: mon1 (1)10.0.0.2:6789 session established
Jul 3 11:03:29 kvm1 mount[4172]: mount error: no mds server is up or the cluster is laggy
Jul 3 11:03:29 kvm1 systemd[1]: mnt-pve-cephfs.mount: Mount process exited, code=exited, status=32/n/a
Jul 3 11:03:29 kvm1 systemd[1]: mnt-pve-cephfs.mount: Failed with result 'exit-code'.
Jul 3 11:03:29 kvm1 systemd[1]: Failed to mount /mnt/pve/cephfs.
Jul 3 11:03:29 kvm1 kernel: [ 162.289385] libceph: client82474275 fsid c2f2d56b-77d3-4c42-bbba-748d86cc2e2a
Jul 3 11:03:29 kvm1 kernel: [ 162.289433] ceph: No mds server is up or the cluster is laggy
Jul 3 11:03:29 kvm1 pvestatd[2195]: mount error: See "systemctl status mnt-pve-cephfs.mount" and "journalctl -xe" for details.