You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Hello. Yes, the token is privilege seperated.is the token privilege separated? could you check the output ofpveum user permissions FULL_TOKEN_ID?
Also where can I run the command above? I'm sort of new to this.
Yes, I just double checked that the token is the correct one because it's the only one that exists. Other than that Packer gives this full error:can you double check that this is actually the token used for the request? can you dump the full request and response or extract it from a log somewhere (censor any sensitive parts like the token secret)..
Error creating VM: error creating VM: 403 Permission check failed (/nodes/pve2, Sys.Audit), error status: (params: map[agent:1 args: boot:c cores:1 cpu:kvm64 description;Packer ephemeral build VM hotplug: ide2:local:iso/ubuntu-20.04.4-live-server-amd64.iso,media=cdrom kvm:true machine: memory:512 name:crane-cis-w2 net0:virtio=2A:EF:77:F6:3C:8B,bridge=vmbr0,firewall=false numa:false onboot:false ostype;other scsihw:virtio-scsi-pci sockets:1 tablet:false tags: virtio0:zfs-raid-1:20,format=raw,iothread=false vmid:107])
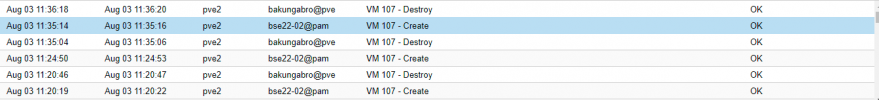
Lastly, I'm not sure how I can get the logs maybe you can help me but when I checked the permissions of the user that shows up under the tasks window when the virtual machine is created. I noticed that they do not have the Sys.Audit permission. Does the user the token is created for need to have the privileges as well?
Last edited:
This is what I can see from the interface. I've tried to run a console but it doesn't seem to connect.which version are you on? (pveversion -v)
and yes, for a privilege-separated token the user and the token need to have a privilege on a path for it to be effective (but there was a display bug in older versions)
Does this help with the version?
Hello, I also faced the described issue in this topic with Proxmox Virtual Environment 7.2-11. I created a new PVE web-user using the GUI and added a token to the user. Assigning only ACL "Administrator" to the token resulted in errors as described in this topic and this is shown below.you can try adding the corresponding user ACL - but please note that PVE 6.x is EOL since last week, so an upgrade to the still supported 7.x release series is required to receive both this and any other future bug fixes.
Adding both ACL for user AND the token allows token ACL to work properly. Not sure if this is intended behavior?
Trying to access PVE-node status with only ACL on Token
Code:
$ https --verify=no -v 172.20.1.2:8006/api2/json/nodes/pve/status authorization:"PVEAPIToken=automation@pve!packer-terraform=random-guid-here"
GET /api2/json/nodes/pve/status HTTP/1.1
Accept: */*
Accept-Encoding: gzip, deflate
Connection: keep-alive
Host: 172.20.1.2:8006
User-Agent: HTTPie/3.2.1
authorization: PVEAPIToken=automation@pve!packer-terraform=random-guid-here
HTTP/1.1 403 Permission check failed (/nodes/pve, Sys.Audit)
Cache-Control: max-age=0
Connection: close
Content-Length: 13
Content-Type: application/json;charset=UTF-8
Date: Fri, 28 Oct 2022 11:38:38 GMT
Expires: Fri, 28 Oct 2022 11:38:38 GMT
Pragma: no-cache
Server: pve-api-daemon/3.0
{
"data": null
}
yes, this is intentional and documented  https://pve.proxmox.com/pve-docs/chapter-pveum.html#pveum_tokens
https://pve.proxmox.com/pve-docs/chapter-pveum.html#pveum_tokens
there are tokens that get all the privileges of the user (with no way of restricting further) and tokens that get no privileges by default, but can get any privilege within the boundaries of those of the user (so for example, an Administrator user can create a token with only Auditor privileges, or Administrator privileges but only on some paths not everywhere the user itself has them, etc.pp.).
there are tokens that get all the privileges of the user (with no way of restricting further) and tokens that get no privileges by default, but can get any privilege within the boundaries of those of the user (so for example, an Administrator user can create a token with only Auditor privileges, or Administrator privileges but only on some paths not everywhere the user itself has them, etc.pp.).