I see that Proxmox has support for iSCSI with two different drivers: kernel open-iscsi and user-mode libiscsi2. While this isn't specified in the docs I found out that the kernel one is supposed to be attached to the host and create block device, which is then passed through to the guest. This, besides lower performance, seems to imply that Proxmox must create a datastore on it. This is not what I want, as I already have exposed LUNs with existing data on the NAS, e.g.:
I tried adding the iSCSI to
However, I cannot find ANY documentation or examples on how to attach a LUN from such a backend to a VM. I see that QEMU has docs around their iSCSI but I would rather not go around and use
Using
Any help would be appreciated
Code:
# fdisk -l /dev/zvol/ssd-dev/iscsi-iot04dev1
Disk /dev/zvol/ssd-dev/iscsi-iot04dev1: 32 GiB, 34359738368 bytes, 67108864 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 16384 bytes
I/O size (minimum/optimal): 16384 bytes / 16384 bytes
Disklabel type: gpt
Disk identifier: ***
Device Start End Sectors Size Type
/dev/zvol/ssd-dev/iscsi-iot04dev11 2048 67583 65536 32M EFI System
/dev/zvol/ssd-dev/iscsi-iot04dev12 67584 116735 49152 24M Linux filesystem
(...)I tried adding the iSCSI to
/etc/pve/storage.cfg using iscsidirect driver:
Code:
iscsidirect: iscsi-iot04dev
portal store-XXX-int.AAA.BBB
target iqn.2000-01.BBB.AAA.store-XXX-int:iscsiHowever, I cannot find ANY documentation or examples on how to attach a LUN from such a backend to a VM. I see that QEMU has docs around their iSCSI but I would rather not go around and use
args: hack. For the record, in case someone finds this thread in the future, it does indeed work, albeit only in OVMF (UEFI) mode:
Code:
# cat /etc/pve/qemu-server/192.conf
args: -drive file=iscsi://store-XXX-int.AAA.BBB/iqn.2000-01.BBB.AAA.store-XXX-int:iscsi/43
bios: ovmf
cpu: host
(...)Using
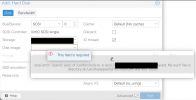
args: hides it from the WebUI and also doesn't seem like the correct/Proxmox-way of adding it. I tried using the WebUI and the "Add: Hard Disk" wizard but it simply errors out:
Any help would be appreciated
Last edited: