Hello!
I am an admitted newbie here so forgive my general ignorance! I have Proxmox VE running with Docker in an LXC (on reflection I should have just ran my docker containers as LXCs but we are where we are!), with an external hard drive as a media drive. This has been operating mostly smoothly for the past 6 months or so. I was doing a bit of office reorganisation earlier today, and after shutting down and eventually rebooting the server, I'm now having issues with the mount for the external HDD.
The mount was set up through the Proxmox GUI, and when I boot the server up it all appears normally without any errors. I can see CT volumes and templates and stats about drive usage etc. without issue. However once the Docker LXC starts, the mounted HDD becomes unavailable with the error 'unable to activate storage - directory is expected to be a mount point but is not mounted'.
I can only assume something about the interaction between the Docker LXC and the mounted HDD is causing the issue. Nothing has changed about the configuration since the server rebooted and broke the mount, and I'm running up against my lack of know-how in trying to fix it!
This is how the container/mount point is configured for the LXC:
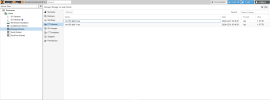
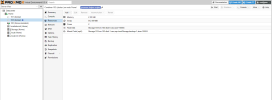
I'm mostly concerned with preserving the data on the HDD if possible, as I know it can be easy to lose data if you're not careful with this kind of thing.
Below are some of the shell outputs that I've had in trying to diagnose the issue, in case these are of any help.
Thanks in advance!
I am an admitted newbie here so forgive my general ignorance! I have Proxmox VE running with Docker in an LXC (on reflection I should have just ran my docker containers as LXCs but we are where we are!), with an external hard drive as a media drive. This has been operating mostly smoothly for the past 6 months or so. I was doing a bit of office reorganisation earlier today, and after shutting down and eventually rebooting the server, I'm now having issues with the mount for the external HDD.
The mount was set up through the Proxmox GUI, and when I boot the server up it all appears normally without any errors. I can see CT volumes and templates and stats about drive usage etc. without issue. However once the Docker LXC starts, the mounted HDD becomes unavailable with the error 'unable to activate storage - directory is expected to be a mount point but is not mounted'.

I can only assume something about the interaction between the Docker LXC and the mounted HDD is causing the issue. Nothing has changed about the configuration since the server rebooted and broke the mount, and I'm running up against my lack of know-how in trying to fix it!
This is how the container/mount point is configured for the LXC:


I'm mostly concerned with preserving the data on the HDD if possible, as I know it can be easy to lose data if you're not careful with this kind of thing.
Below are some of the shell outputs that I've had in trying to diagnose the issue, in case these are of any help.
Thanks in advance!
Code:
root@Home:~# lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINTS
sda 8:0 0 447.1G 0 disk
├─sda1 8:1 0 1007K 0 part
├─sda2 8:2 0 1G 0 part
└─sda3 8:3 0 446.1G 0 part
├─pve-swap 253:0 0 7.7G 0 lvm [SWAP]
├─pve-root 253:1 0 96G 0 lvm /
├─pve-data_tmeta 253:2 0 3.3G 0 lvm
│ └─pve-data-tpool 253:4 0 319.9G 0 lvm
│ ├─pve-data 253:5 0 319.9G 1 lvm
│ ├─pve-vm--100--disk--0 253:6 0 4M 0 lvm
│ └─pve-vm--100--disk--2 253:7 0 32G 0 lvm
└─pve-data_tdata 253:3 0 319.9G 0 lvm
└─pve-data-tpool 253:4 0 319.9G 0 lvm
├─pve-data 253:5 0 319.9G 1 lvm
├─pve-vm--100--disk--0 253:6 0 4M 0 lvm
└─pve-vm--100--disk--2 253:7 0 32G 0 lvm
sdb 8:16 0 1.8T 0 disk
└─sdb1 8:17 0 1.8T 0 part /mnt/pve/Storage
Code:
root@Home:~# cat /etc/pve/storage.cfg
dir: local
path /var/lib/vz
content vztmpl,iso,backup
lvmthin: local-lvm
thinpool data
vgname pve
content rootdir,images
dir: Storage
path /mnt/pve/Storage
content backup,images,snippets,rootdir,vztmpl,iso
is_mountpoint 1
nodes Home
Code:
root@Home:~# systemctl status mnt-pve-Storage.mount
● mnt-pve-Storage.mount - Mount storage 'Storage' under /mnt/pve
Loaded: loaded (/etc/systemd/system/mnt-pve-Storage.mount; enabled; preset: enabled)
Active: active (mounted) since Wed 2024-02-21 03:40:45 GMT; 11min ago
Where: /mnt/pve/Storage
What: /dev/sdb1
Tasks: 0 (limit: 9318)
Memory: 8.0K
CPU: 7ms
CGroup: /system.slice/mnt-pve-Storage.mount
Feb 21 03:40:44 Home systemd[1]: Mounting mnt-pve-Storage.mount - Mount storage 'Storage' under /mnt/pve...
Feb 21 03:40:45 Home systemd[1]: Mounted mnt-pve-Storage.mount - Mount storage 'Storage' under /mnt/pve.
Code:
Disk /dev/sdb: 1.82 TiB, 2000398933504 bytes, 3907029167 sectors
Disk model: Expansion
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 4096 bytes
I/O size (minimum/optimal): 4096 bytes / 4096 bytes
Disklabel type: gpt
Disk identifier: 2B890620-F14F-4821-8A01-20F3E364D2D0
Device Start End Sectors Size Type
/dev/sdb1 2048 3907029133 3907027086 1.8T Linux filesystem
Code:
root@Home:~# cat /etc/fstab
# <file system> <mount point> <type> <options> <dump> <pass>
/dev/pve/root / ext4 errors=remount-ro 0 1
/dev/pve/swap none swap sw 0 0
proc /proc proc defaults 0 0
#/dev/sdb1
UUID=2198105b-0336-4937-8919-95210637874d /mnt/pve/Storage xfs defaults 0 0
Last edited: