Hi guys,
I am new to Proxmox, and I am loving it. I am just wondering if I can still achieve a good Proxmox Virtualization with proper networking
8 x Intel(R) Xeon(R) CPU E3-1231 v3 @ 3.40GHz (1 Socket)
32gb RAM
2x 500 GB SSD
1x IPv4
This is a Hosting Dedicated Server (Old Server from a friend of mine [given to me now] that he bought from a VPS/DDS Provider)
What i want to achieve:
1. Have a private network with internet access
2. Have each new VM a IP from the private network (if possible)
What have i done:
1. Installed Promox 7.4.x
2. Can access the Proxmox via Static IP
3. Add pve-no-subscription
4. Tried to tinker with the vmbr1 (192.168.10.1/24)
5. No IP given to the VM
6. Set Static IP of VM still no internet
Some image of what I have done.
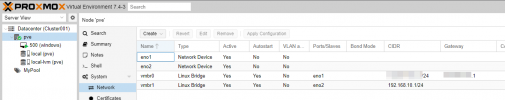
Let me know what I can do to make it work, or what I am doing wrong. Thank you in advanced!
I am new to Proxmox, and I am loving it. I am just wondering if I can still achieve a good Proxmox Virtualization with proper networking
8 x Intel(R) Xeon(R) CPU E3-1231 v3 @ 3.40GHz (1 Socket)
32gb RAM
2x 500 GB SSD
1x IPv4
This is a Hosting Dedicated Server (Old Server from a friend of mine [given to me now] that he bought from a VPS/DDS Provider)
What i want to achieve:
1. Have a private network with internet access
2. Have each new VM a IP from the private network (if possible)
What have i done:
1. Installed Promox 7.4.x
2. Can access the Proxmox via Static IP
3. Add pve-no-subscription
4. Tried to tinker with the vmbr1 (192.168.10.1/24)
5. No IP given to the VM
6. Set Static IP of VM still no internet
Some image of what I have done.

Let me know what I can do to make it work, or what I am doing wrong. Thank you in advanced!
Last edited:

