I would like to host a pair of web applications in LCXs on a server, with one unique public IP address.
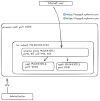
I have created a simple zone in SDN, created a subnet 192.168.100.0/24
LCX are attached the the SDN zone, and they get their IP addresses.
LCXs have access to the internet, and to the LAN (this is unwanted)
I have 3 LXCs;
The internet router sends the 80 and the 443 traffic to the proxmox server.
The proxmox incoming traffic on port 80 and 443 is forwarded to the reverse proxy using iptables -nat instructions on the proxmox server.
The reverse proxy (caddy) is doing the SSL termination and tries to route the traffic to applications various containers (as visible in the logs)
At this point:
- The communication between the reverse proxy and the containers is blocked
- The reverse proxy serves the external urls, but fails to contact the application container
- each container can access to the internet
- but each container can access the the lan, which is unwanted
What I'm doing wrong?
Is there some tutorial / comprehensible docs I can read?
thanks for your help

I have created a simple zone in SDN, created a subnet 192.168.100.0/24
LCX are attached the the SDN zone, and they get their IP addresses.
LCXs have access to the internet, and to the LAN (this is unwanted)
I have 3 LXCs;
- The reverse proxy (caddy)
- The app1,that is listening http traffic on it's own port
- The app2, that is listening http traffic on it's own port
The internet router sends the 80 and the 443 traffic to the proxmox server.
The proxmox incoming traffic on port 80 and 443 is forwarded to the reverse proxy using iptables -nat instructions on the proxmox server.
The reverse proxy (caddy) is doing the SSL termination and tries to route the traffic to applications various containers (as visible in the logs)
At this point:
- The communication between the reverse proxy and the containers is blocked
- The reverse proxy serves the external urls, but fails to contact the application container
- each container can access to the internet
- but each container can access the the lan, which is unwanted
What I'm doing wrong?
Is there some tutorial / comprehensible docs I can read?
thanks for your help


