Hello. PVE is:
I have vm (lets name it as VM1), where some sort of third party software was installed by remote support, I don' have passwords or any access to this vm. I know only ip address.
Next, I found that my other debian vm(s) (VM2) have a long time to bring their network alive. They boot fast, I connect from gui console: networking service is ok and links up. But network dont work. After some time (~2 min) vm become accessable.
After some research I found that VM1 answering for arp requests and saying that gateway is VM1 it self:
where 192.168.200.71 is my VM2 ip, and b6:e2:64:46:ff:37 is VM1 mac address. As you can see, VM1 answer to VM2 and VM2 get wrong gw for some period of time.
I try to enable firewall and MAC/IP filters - no results.
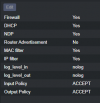
How can I prevent this behaviour ? How to protect vm from arp spoofing ?
Thanks!
proxmox-ve: 6.2-1 (running kernel: 5.4.34-1-pve) pve-manager: 6.2-4 (running version: 6.2-4/9824574a) pve-kernel-5.4: 6.2-1 pve-kernel-helper: 6.2-1 pve-kernel-5.4.34-1-pve: 5.4.34-2 ceph-fuse: 12.2.11+dfsg1-2.1+b1 corosync: 3.0.3-pve1 criu: 3.11-3 glusterfs-client: 5.5-3 ifupdown: 0.8.35+pve1 ksm-control-daemon: 1.3-1 libjs-extjs: 6.0.1-10 libknet1: 1.15-pve1 libproxmox-acme-perl: 1.0.3 libpve-access-control: 6.1-1 libpve-apiclient-perl: 3.0-3 libpve-common-perl: 6.1-2 libpve-guest-common-perl: 3.0-10 libpve-http-server-perl: 3.0-5 libpve-storage-perl: 6.1-7 libqb0: 1.0.5-1 libspice-server1: 0.14.2-4~pve6+1 lvm2: 2.03.02-pve4 lxc-pve: 4.0.2-1 lxcfs: 4.0.3-pve2 novnc-pve: 1.1.0-1 proxmox-mini-journalreader: 1.1-1 proxmox-widget-toolkit: 2.2-1 pve-cluster: 6.1-8 pve-container: 3.1-5 pve-docs: 6.2-4 pve-edk2-firmware: 2.20200229-1 pve-firewall: 4.1-2 pve-firmware: 3.1-1 pve-ha-manager: 3.0-9 pve-i18n: 2.1-2 pve-qemu-kvm: 5.0.0-2 pve-xtermjs: 4.3.0-1 qemu-server: 6.2-2 smartmontools: 7.1-pve2 spiceterm: 3.1-1 vncterm: 1.6-1 zfsutils-linux: 0.8.3-pve1
I have vm (lets name it as VM1), where some sort of third party software was installed by remote support, I don' have passwords or any access to this vm. I know only ip address.
Next, I found that my other debian vm(s) (VM2) have a long time to bring their network alive. They boot fast, I connect from gui console: networking service is ok and links up. But network dont work. After some time (~2 min) vm become accessable.
After some research I found that VM1 answering for arp requests and saying that gateway is VM1 it self:
Code:
tcpdump -n -i tap101i0 host 192.168.200.71
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on tap101i0, link-type EN10MB (Ethernet), capture size 262144 bytes
17:09:47.989368 ARP, Request who-has 192.168.200.70 tell 192.168.200.71, length 46
17:09:48.006433 ARP, Request who-has 192.168.200.1 tell 192.168.200.71, length 46
17:09:48.006570 ARP, Reply 192.168.200.1 is-at b6:e2:64:46:ff:37, length 28where 192.168.200.71 is my VM2 ip, and b6:e2:64:46:ff:37 is VM1 mac address. As you can see, VM1 answer to VM2 and VM2 get wrong gw for some period of time.
I try to enable firewall and MAC/IP filters - no results.

How can I prevent this behaviour ? How to protect vm from arp spoofing ?
Thanks!

