Hi there,
I'm trying to passthrough my wifi+bt card (QCA6174) to for the home assistant vm, I got the bluetooth via usb (I didn't do in-depth tests, but the HA recognized it), I'm trying to passthrough the wifi to another ubuntu vm to test, but the idea is to use it on the HA too, but always when I add the PCI device, proxmox and all vm's goes offline and I have to edit directly in the .conf to remove the PCI and go back online
From what I researched, I believe this happens because my onboard ethernet NIC is in the same IOMMU group as the wifi card (group 7), I tried using "pci_acs_override", it activates (I have in the log Warning: PCIe ACS overrides enabled; This may allow non -IOMMU protected peer-to-peer DMA) but the groups do not change, I tried the following ways by changing the grub:
update grub and reboot.
The result is the same, is there something I'm doing wrong?
My setup:
Dell Optiplex 3080
I5-10400t
pve-manager/8.0.4
(running kernel: 6.2.16-12-pve)
My output of
A screenshot for a better view:
I saw something about recompiling the kernel, if I'm not mistaken, making some changes such as removing the pci_find_ext_capability(dev, PCI_EXT_CAP_ID_ACS)) line, would this be the way to go?
Thanks.
I'm trying to passthrough my wifi+bt card (QCA6174) to for the home assistant vm, I got the bluetooth via usb (I didn't do in-depth tests, but the HA recognized it), I'm trying to passthrough the wifi to another ubuntu vm to test, but the idea is to use it on the HA too, but always when I add the PCI device, proxmox and all vm's goes offline and I have to edit directly in the .conf to remove the PCI and go back online
From what I researched, I believe this happens because my onboard ethernet NIC is in the same IOMMU group as the wifi card (group 7), I tried using "pci_acs_override", it activates (I have in the log Warning: PCIe ACS overrides enabled; This may allow non -IOMMU protected peer-to-peer DMA) but the groups do not change, I tried the following ways by changing the grub:
GRUB_CMDLINE_LINUX_DEFAULT="quiet intel_iommu=on iommu=pt pcie_acs_override=downstream"
GRUB_CMDLINE_LINUX_DEFAULT="quiet intel_iommu=on iommu=pt pcie_acs_override=downstream,multifunction"update grub and reboot.
The result is the same, is there something I'm doing wrong?
My setup:
Dell Optiplex 3080
I5-10400t
pve-manager/8.0.4
(running kernel: 6.2.16-12-pve)
My output of
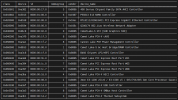
for d in /sys/kernel/iommu_groups/*/devices/*; do n=${d#*/iommu_groups/*}; n=${n%%/*}; printf 'IOMMU group %s ' "$n"; lspci -nns "${d##*/}"; done :
IOMMU group 0 00:02.0 VGA compatible controller [0300]: Intel Corporation CometLake-S GT2 [UHD Graphics 630] [8086:9bc8] (rev 03)
IOMMU group 1 00:00.0 Host bridge [0600]: Intel Corporation Comet Lake-S 6c Host Bridge/DRAM Controller [8086:9b53] (rev 03)
IOMMU group 2 00:08.0 System peripheral [0880]: Intel Corporation Xeon E3-1200 v5/v6 / E3-1500 v5 / 6th/7th/8th Gen Core Processor Gaussian Mixture Model [8086:1911]
IOMMU group 3 00:14.0 USB controller [0c03]: Intel Corporation Comet Lake PCH-V USB Controller [8086:a3af]
IOMMU group 3 00:14.2 Signal processing controller [1180]: Intel Corporation Comet Lake PCH-V Thermal Subsystem [8086:a3b1]
IOMMU group 4 00:16.0 Communication controller [0780]: Intel Corporation Comet Lake PCH-V HECI Controller [8086:a3ba]
IOMMU group 5 00:17.0 SATA controller [0106]: Intel Corporation 400 Series Chipset Family SATA AHCI Controller [8086:a382]
IOMMU group 6 00:1b.0 PCI bridge [0604]: Intel Corporation Comet Lake PCI Express Root Port #21 [8086:a3eb] (rev f0)
IOMMU group 6 01:00.0 Non-Volatile memory controller [0108]: Phison Electronics Corporation PS5013 E13 NVMe Controller [1987:5013] (rev 01)
IOMMU group 7 00:1c.0 PCI bridge [0604]: Intel Corporation Comet Lake PCI Express Root Port #05 [8086:a394] (rev f0)
IOMMU group 7 00:1c.7 PCI bridge [0604]: Intel Corporation Comet Lake PCI Express Root Port #08 [8086:a397] (rev f0)
IOMMU group 7 02:00.0 Ethernet controller [0200]: Realtek Semiconductor Co., Ltd. RTL8111/8168/8411 PCI Express Gigabit Ethernet Controller [10ec:8168] (rev 15)
IOMMU group 7 03:00.0 Network controller [0280]: Qualcomm Atheros QCA6174 802.11ac Wireless Network Adapter [168c:003e] (rev 32)
IOMMU group 8 00:1f.0 ISA bridge [0601]: Intel Corporation B460 Chipset LPC/eSPI Controller [8086:a3c8]
IOMMU group 8 00:1f.2 Memory controller [0580]: Intel Corporation Cannon Lake PCH Power Management Controller [8086:a3a1]
IOMMU group 8 00:1f.3 Audio device [0403]: Intel Corporation Comet Lake PCH-V cAVS [8086:a3f0]
IOMMU group 8 00:1f.4 SMBus [0c05]: Intel Corporation Comet Lake PCH-V SMBus Host Controller [8086:a3a3]A screenshot for a better view:

I saw something about recompiling the kernel, if I'm not mistaken, making some changes such as removing the pci_find_ext_capability(dev, PCI_EXT_CAP_ID_ACS)) line, would this be the way to go?
Thanks.

