I'm trying to configure OIDC authentication to go through Server 2022 ADFS. Following a few guides out there about different products, I've stitched together a configuration that seems to be about 90% complete. Currently, I get the error
Any ideas where I'm wrong or next steps on troubleshooting this? I tried starting pvedaemon with
OIDC Configuration
ADFS Server Application
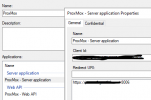
ADFS Web Server API
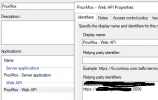
ADFS Issuance Transform Rules
OpenID login failed, please try again authentication failure (401) in the WebUI andpvedaemon[3108070]: openid authentication failure; rhost=192.168.1.194 msg=Failed to contact userinfo endpoint: Request failed is logged in syslog.Any ideas where I'm wrong or next steps on troubleshooting this? I tried starting pvedaemon with
--debug 0, but it didn't seem to do anything.OIDC Configuration
Code:
openid: OIDC
client-id xxxxxxxxxxxxxx
issuer-url https://adfs.contoso.net/adfs
autocreate 1
client-key xxxxxxxxxxxxxxx
default 0
username-claim emailADFS Server Application

ADFS Web Server API

ADFS Issuance Transform Rules


