In short, I am trying to get a pfSense VM within proxmox to be my main network router/firewall.
truths:
Here's my switch config (Cisco Catalyst3560)
Server's NIC (eno3) is plugged into the above 0/3 interface.
Proxmox's /etc/network/interface (only relevant sections):
I need to step away for a bit, but will respond with more information (things I've tried) when I return.
truths:
- I can connect to proxmox's management interface (10.1.0.10)
- I can connect to pfSense's management interface (10.1.0.1)
- I can ping vlan interfaces on pfSense (10.3.0.1) from my physical workstation (10.1.0.99)
- I cannot ping the 10.3.0.1 gateway from a virtual server located on the same network (10.3.0.10)
- pfSense has firewall on its 10.3.0.0/24 interface to allow any/any
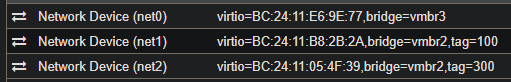
- pfSense has a vNIC on vmbr2,tag=100
- pfSense LAN is vtnet1 (the above vNIC) with IP: 10.1.0.1
- pfSense OPT1 is vtnet1.300 with IP 10.3.0.1
- I am a Linux virtual networking noob, so I believe it is a misconfiguration on my part
Here's my switch config (Cisco Catalyst3560)
Code:
# show run interface gi 0/3
interface GigabitEhternet0/3
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 100,200,300
switchport mode trunk
endServer's NIC (eno3) is plugged into the above 0/3 interface.
Proxmox's /etc/network/interface (only relevant sections):
Code:
auto lo
iface lo inet loopback
auto eno3
iface eno3 inet manual
auto vmbr2
iface vmbr2 inet manual
bridge-ports eno3
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 2-4094
auto vmbr2.100
iface vmbr2.100 inet static
address 10.1.0.10/24
gateway 10.1.0.1
#Proxmox management interface
auto vmbr2.300
iface vmbr2.300 inet manual
I need to step away for a bit, but will respond with more information (things I've tried) when I return.