Hi,
I currently have a modified PVE 8.1.x
And I'm stuck on a small problem defining via ipset.
I can't use my firewall as I would like.My configuration works on a classic PVE.
But here I tell myself that I probably forgot a defconfig side for the kernel.
Do you have any ideas or recommendations on this?
Best Regards
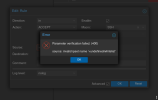
I currently have a modified PVE 8.1.x
And I'm stuck on a small problem defining via ipset.
I can't use my firewall as I would like.My configuration works on a classic PVE.
But here I tell myself that I probably forgot a defconfig side for the kernel.
Do you have any ideas or recommendations on this?
Best Regards

Code:
Jan 26 12:15:58 sv1 pve-firewall[4109]: /etc/pve/firewall/cluster.fw (line 25) - errors in rule parameters: IN HTTPS(ACCEPT) -source +dc/whitelist -log nolog
Jan 26 12:15:58 sv1 pve-firewall[4109]: source: invalid ipset name '+dc/whitelist'
Jan 26 12:16:08 sv1 pve-firewall[4109]: /etc/pve/firewall/cluster.fw (line 21) - errors in rule parameters: IN Ping(ACCEPT) -source +dc/whitelist -log nolog
Jan 26 12:16:08 sv1 pve-firewall[4109]: source: invalid ipset name '+dc/whitelist'
Jan 26 12:16:08 sv1 pve-firewall[4109]: /etc/pve/firewall/cluster.fw (line 22) - errors in rule parameters: IN ACCEPT -source +dc/whitelist -p tcp -dport 800>
Jan 26 12:16:08 sv1 pve-firewall[4109]: source: invalid ipset name '+dc/whitelist'
Jan 26 12:16:08 sv1 pve-firewall[4109]: /etc/pve/firewall/cluster.fw (line 23) - errors in rule parameters: IN SSH(ACCEPT) -source +dc/whitelist -log nolog
Jan 26 12:16:08 sv1 pve-firewall[4109]: source: invalid ipset name '+dc/whitelist'
Jan 26 12:16:08 sv1 pve-firewall[4109]: /etc/pve/firewall/cluster.fw (line 25) - errors in rule parameters: IN HTTPS(ACCEPT) -source +dc/whitelist -log nolog
Jan 26 12:16:08 sv1 pve-firewall[4109]: source: invalid ipset name '+dc/whitelist'
Last edited:

