Hello, can someone help me with port forwarding in Proxmox VE 8.0.3? I want to configure access using my public IP address so that I can still access the virtual environment when I'm outside my network. I have set up port forwarding in my router (see images), but when I try to access it from xxx.x.xx.xxx:9000, I get a connection timeout error.
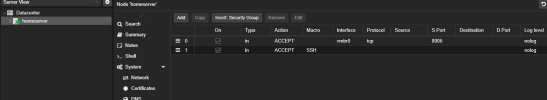
The firewall in Proxmox VE is active and only port 8006 is open on both the data center and node.
My local Proxmox connection is 192.168.0.14:8006.
What could be missing in this configuration?
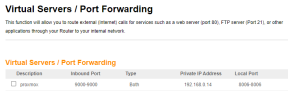 (router)
(router)
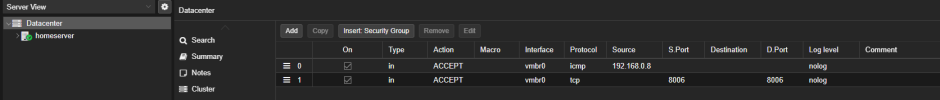
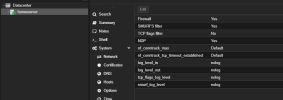
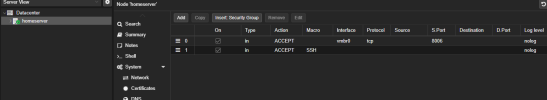
The firewall in Proxmox VE is active and only port 8006 is open on both the data center and node.
My local Proxmox connection is 192.168.0.14:8006.
What could be missing in this configuration?
 (router)
(router)