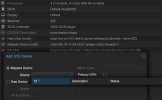
I've been through everything in the BIOS line by line and enabled everything I could find that even seemed at all related but I still get the same error when I try to add a PCI device to a VM in Proxmox VE:
There's only a single CPU installed at the moment so there might be some MPS options disabled in the BIOS but that shouldn't be hiding IOMMU or VT-d features?
I knew there would be no AVX support and such with an older board, but wasn't expecting PCI passthrough problems.
Web searches hint that I may not have had the right CPU features enabled when I did the initial install and the bootloader may need to be reconfigured to enable IOMMU but none of the tips (ie: add
TIA for any insights/experience.
Code:
No IOMMU detected, please activate it.See Documentation for further information.There's only a single CPU installed at the moment so there might be some MPS options disabled in the BIOS but that shouldn't be hiding IOMMU or VT-d features?
I knew there would be no AVX support and such with an older board, but wasn't expecting PCI passthrough problems.
Web searches hint that I may not have had the right CPU features enabled when I did the initial install and the bootloader may need to be reconfigured to enable IOMMU but none of the tips (ie: add
intel_iommu=on to /etc/kernel/cmdline) seem to be related to the PVE server I've got running (the cmdline file does not exist)?TIA for any insights/experience.