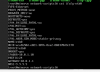
Chain INPUT (policy ACCEPT)
target prot opt source destination
f2b-proxmox tcp -- anywhere anywhere multiport dports https,http,8006
f2b-sshd tcp -- anywhere anywhere multiport dports ssh
PVEFW-INPUT all -- anywhere anywhere
Chain FORWARD (policy ACCEPT)
target prot opt source destination
PVEFW-FORWARD all -- anywhere anywhere
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
PVEFW-OUTPUT all -- anywhere anywhere
Chain PVEFW-Drop (2 references)
target prot opt source destination
PVEFW-reject tcp -- anywhere anywhere tcp dpt:whois
PVEFW-DropBroadcast all -- anywhere anywhere
ACCEPT icmp -- anywhere anywhere icmp fragmentation-needed
ACCEPT icmp -- anywhere anywhere icmp time-exceeded
DROP all -- anywhere anywhere ctstate INVALID
DROP udp -- anywhere anywhere multiport dports loc-srv,microsoft-ds
DROP udp -- anywhere anywhere udp dpts:netbios-ns:netbios-ssn
DROP udp -- anywhere anywhere udp spt:netbios-ns dpts:1024:65535
DROP tcp -- anywhere anywhere multiport dports loc-srv,netbios-ssn,microsoft-ds
DROP udp -- anywhere anywhere udp dpt:1900
DROP tcp -- anywhere anywhere tcp flags:!FIN,SYN,RST,ACK/SYN
DROP udp -- anywhere anywhere udp spt:domain
all -- anywhere anywhere /* PVESIG:WDy2wbFe7jNYEyoO3QhUELZ4mIQ */
Chain PVEFW-DropBroadcast (2 references)
target prot opt source destination
DROP all -- anywhere anywhere ADDRTYPE match dst-type BROADCAST
DROP all -- anywhere anywhere ADDRTYPE match dst-type MULTICAST
DROP all -- anywhere anywhere ADDRTYPE match dst-type ANYCAST
DROP all -- anywhere base-address.mcast.net/4
all -- anywhere anywhere /* PVESIG:NyjHNAtFbkH7WGLamPpdVnxHy4w */
Chain PVEFW-FORWARD (1 references)
target prot opt source destination
DROP all -- anywhere anywhere ctstate INVALID
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
PVEFW-FWBR-IN all -- anywhere anywhere PHYSDEV match --physdev-in fwln+ --physdev-is-bridged
PVEFW-FWBR-OUT all -- anywhere anywhere PHYSDEV match --physdev-out fwln+ --physdev-is-bridged
all -- anywhere anywhere /* PVESIG:qnNexOcGa+y+jebd4dAUqFSp5nw */
Chain PVEFW-FWBR-IN (1 references)
target prot opt source destination
PVEFW-smurfs all -- anywhere anywhere ctstate INVALID,NEW
tap100i0-IN all -- anywhere anywhere PHYSDEV match --physdev-out tap100i0 --physdev-is-bridged
all -- anywhere anywhere /* PVESIG:/naDZxJ06t8Dx9DQtmus9NvdHEA */
Chain PVEFW-FWBR-OUT (1 references)
target prot opt source destination
tap100i0-OUT all -- anywhere anywhere PHYSDEV match --physdev-in tap100i0 --physdev-is-bridged
all -- anywhere anywhere /* PVESIG:wA3mj3VIKyC/rlY95PCFN7paR5s */
Chain PVEFW-HOST-IN (1 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere
DROP all -- anywhere anywhere ctstate INVALID
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
PVEFW-smurfs all -- anywhere anywhere ctstate INVALID,NEW
RETURN igmp -- anywhere anywhere
RETURN tcp -- anywhere anywhere tcp dpts:5900:5999
RETURN tcp -- anywhere anywhere tcp dpt:8006
RETURN icmp -- anywhere anywhere icmp echo-request
RETURN udp -- anywhere anywhere udp dpt:ntp
RETURN tcp -- anywhere anywhere tcp dpt:http
RETURN tcp -- anywhere anywhere tcp dpt:ssh
RETURN tcp -- anywhere anywhere match-set PVEFW-0-management-v4 src tcp dpt:8006
RETURN tcp -- anywhere anywhere match-set PVEFW-0-management-v4 src tcp dpts:5900:5999
RETURN tcp -- anywhere anywhere match-set PVEFW-0-management-v4 src tcp dpt:3128
RETURN tcp -- anywhere anywhere match-set PVEFW-0-management-v4 src tcp dpt:ssh
RETURN udp -- xx.xx.xx.0/24 xx.xx.xx.0/24 udp dpts:5404:5405
RETURN udp -- xx.xx.xx.0/24 anywhere ADDRTYPE match dst-type MULTICAST udp dpts:5404:5405
PVEFW-Drop all -- anywhere anywhere
NFLOG all -- anywhere anywhere nflog-prefix ":0:1:PVEFW-HOST-IN: policy DROP: "
DROP all -- anywhere anywhere
all -- anywhere anywhere /* PVESIG:caQnOQIumkbqNPfsPfondzVQBdQ */
Chain PVEFW-HOST-OUT (1 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere
DROP all -- anywhere anywhere ctstate INVALID
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
RETURN igmp -- anywhere anywhere
RETURN tcp -- anywhere xx.xx.xx..0/24 tcp dpt:8006
RETURN tcp -- anywhere xx.xx.xx.0/24 tcp dpt:ssh
RETURN tcp -- anywhere xx.xx.xx.0/24 tcp dpts:5900:5999
RETURN tcp -- anywhere xx.xx.xx.0/24 tcp dpt:3128
RETURN udp -- anywhere xx.xx.xx.0/24 udp dpts:5404:5405
RETURN udp -- anywhere anywhere ADDRTYPE match dst-type MULTICAST udp dpts:5404:5405
RETURN all -- anywhere anywhere
all -- anywhere anywhere /* PVESIG:3yAcVpr0ewHg8DxFR7g9C8B8xxE */
Chain PVEFW-INPUT (1 references)
target prot opt source destination
PVEFW-HOST-IN all -- anywhere anywhere
all -- anywhere anywhere /* PVESIG:+5iMmLaxKXynOB/+5xibfx7WhFk */
Chain PVEFW-OUTPUT (1 references)
target prot opt source destination
PVEFW-HOST-OUT all -- anywhere anywhere
all -- anywhere anywhere /* PVESIG:LjHoZeSSiWAG3+2ZAyL/xuEehd0 */
Chain PVEFW-Reject (0 references)
target prot opt source destination
PVEFW-reject tcp -- anywhere anywhere tcp dpt:whois
PVEFW-DropBroadcast all -- anywhere anywhere
ACCEPT icmp -- anywhere anywhere icmp fragmentation-needed
ACCEPT icmp -- anywhere anywhere icmp time-exceeded
DROP all -- anywhere anywhere ctstate INVALID
PVEFW-reject udp -- anywhere anywhere multiport dports loc-srv,microsoft-ds
PVEFW-reject udp -- anywhere anywhere udp dpts:netbios-ns:netbios-ssn
PVEFW-reject udp -- anywhere anywhere udp spt:netbios-ns dpts:1024:65535
PVEFW-reject tcp -- anywhere anywhere multiport dports loc-srv,netbios-ssn,microsoft-ds
DROP udp -- anywhere anywhere udp dpt:1900
DROP tcp -- anywhere anywhere tcp flags:!FIN,SYN,RST,ACK/SYN
DROP udp -- anywhere anywhere udp spt:domain
all -- anywhere anywhere /* PVESIG:CZJnIN6rAdpu+ej59QPr9+laMUo */
Chain PVEFW-SET-ACCEPT-MARK (2 references)
target prot opt source destination
MARK all -- anywhere anywhere MARK or 0x80000000
all -- anywhere anywhere /* PVESIG:Hg/OIgIwJChBUcWU8Xnjhdd2jUY */
Chain PVEFW-logflags (5 references)
target prot opt source destination
NFLOG all -- anywhere anywhere nflog-prefix ":0:1:PVEFW-logflags: DROP: "
DROP all -- anywhere anywhere
all -- anywhere anywhere /* PVESIG:B9JfHztz+i9ARD3xG6Edm8T3MvM */
Chain PVEFW-reject (6 references)
target prot opt source destination
DROP all -- anywhere anywhere ADDRTYPE match dst-type BROADCAST
DROP all -- base-address.mcast.net/4 anywhere
DROP icmp -- anywhere anywhere
REJECT tcp -- anywhere anywhere reject-with tcp-reset
REJECT udp -- anywhere anywhere reject-with icmp-port-unreachable
REJECT icmp -- anywhere anywhere reject-with icmp-host-unreachable
REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
all -- anywhere anywhere /* PVESIG:Jlkrtle1mDdtxDeI9QaDSL++Npc */
Chain PVEFW-smurflog (2 references)
target prot opt source destination
NFLOG all -- anywhere anywhere nflog-prefix ":0:1:PVEFW-smurflog: DROP: "
DROP all -- anywhere anywhere
all -- anywhere anywhere /* PVESIG:U0bhVR22AI+578udCidFZuCZn7s */
Chain PVEFW-smurfs (2 references)
target prot opt source destination
RETURN all -- default anywhere
PVEFW-smurflog all -- anywhere anywhere [goto] ADDRTYPE match src-type BROADCAST
PVEFW-smurflog all -- base-address.mcast.net/4 anywhere [goto]
all -- anywhere anywhere /* PVESIG:HssVe5QCBXd5mc9kC88749+7fag */
Chain PVEFW-tcpflags (0 references)
target prot opt source destination
PVEFW-logflags tcp -- anywhere anywhere [goto] tcp flags:FIN,SYN,RST,PSH,ACK,URG/FIN,PSH,URG
PVEFW-logflags tcp -- anywhere anywhere [goto] tcp flags:FIN,SYN,RST,PSH,ACK,URG/NONE
PVEFW-logflags tcp -- anywhere anywhere [goto] tcp flags:SYN,RST/SYN,RST
PVEFW-logflags tcp -- anywhere anywhere [goto] tcp flags:FIN,SYN/FIN,SYN
PVEFW-logflags tcp -- anywhere anywhere [goto] tcp spt:0 flags:FIN,SYN,RST,ACK/SYN
all -- anywhere anywhere /* PVESIG:CMFojwNPqllyqD67NeI5m+bP5mo */
Chain f2b-proxmox (1 references)
target prot opt source destination
RETURN all -- anywhere anywhere
Chain f2b-sshd (1 references)
target prot opt source destination
REJECT all -- 220.red-88-3-231.dynamicip.rima-tde.net anywhere reject-with icmp-port-unreachable
REJECT all -- 88.144.55.13 anywhere reject-with icmp-port-unreachable
REJECT all -- na-201-156-122-7.static.avantel.net.mx anywhere reject-with icmp-port-unreachable
REJECT all -- mail46.gtdinternet.com anywhere reject-with icmp-port-unreachable
REJECT all -- 188.166.255.174 anywhere reject-with icmp-port-unreachable
REJECT all -- 185.254.120.6 anywhere reject-with icmp-port-unreachable
REJECT all -- 180.76.155.59 anywhere reject-with icmp-port-unreachable
REJECT all -- 167.99.77.63 anywhere reject-with icmp-port-unreachable
REJECT all -- abts-kk-dynamic-194.172.167.122.airtelbroadband.in anywhere reject-with icmp-port-unreachable
RETURN all -- anywhere anywhere
Chain tap100i0-IN (1 references)
target prot opt source destination
ACCEPT udp -- anywhere anywhere udp spt:bootps dpt:bootpc
ACCEPT icmp -- anywhere anywhere icmp echo-request
ACCEPT tcp -- anywhere anywhere tcp dpt:ssh
PVEFW-Drop all -- anywhere anywhere
NFLOG all -- anywhere anywhere nflog-prefix ":100:3:tap100i0-IN: policy DROP: "
DROP all -- anywhere anywhere
all -- anywhere anywhere /* PVESIG:OjG3yy8rS+mF58lP7OOIlzITKN4 */
Chain tap100i0-OUT (1 references)
target prot opt source destination
PVEFW-SET-ACCEPT-MARK udp -- anywhere anywhere [goto] udp spt:bootpc dpt:bootps
DROP all -- anywhere anywhere MAC ! C6:89:2A:9B:14:52
MARK all -- anywhere anywhere MARK and 0x7fffffff
PVEFW-SET-ACCEPT-MARK all -- anywhere anywhere [goto]
all -- anywhere anywhere /* PVESIG:j+bYiBsPORQKU/flDmr0DuibHFs */