Hi,
Troubleshooted a weird bridging issue just now. We have a vm (VM A) on a proxmox host (HOST A) using a tagged interface (vlan 17). On this interface the firewall option was checked, but the firewall configuration was set to off:
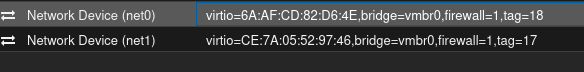
We were sending a TCP SYN packet from another proxmox vm (VM B) on another host (HOST B) to a port on the vm which was not listening. On VM A with a tcpdump we could see the TCP RST being sent to the IP of VM B. On HOST A I could see on vmbr0v17 that the TCP RST packet was received on the bridge. However the packet was not sent to the eno1.17 physical host interface. Only when the firewall option was explicitely removed from the interface (unchecked) I could see the TCP RST being sent on the physical interface.
brctl before the change:
tcpdump on the vmbr0v17:
But then the tcpdump on eno1.17:
Only when I unchecked the firewall option and restarted the VM the TCP RST went through. brctl after the change:
Is this the expected behavior or might this be a bug?
Troubleshooted a weird bridging issue just now. We have a vm (VM A) on a proxmox host (HOST A) using a tagged interface (vlan 17). On this interface the firewall option was checked, but the firewall configuration was set to off:


We were sending a TCP SYN packet from another proxmox vm (VM B) on another host (HOST B) to a port on the vm which was not listening. On VM A with a tcpdump we could see the TCP RST being sent to the IP of VM B. On HOST A I could see on vmbr0v17 that the TCP RST packet was received on the bridge. However the packet was not sent to the eno1.17 physical host interface. Only when the firewall option was explicitely removed from the interface (unchecked) I could see the TCP RST being sent on the physical interface.
brctl before the change:
Code:
:~# brctl show vmbr0v17
bridge name bridge id STP enabled interfaces
vmbr0v17 8000.02cd4b857ce2 no eno1.17
fwpr510p1tcpdump on the vmbr0v17:
Code:
~# tcpdump -n -i vmbr0v17 host A.B.24.34
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on vmbr0v17, link-type EN10MB (Ethernet), snapshot length 262144 bytes
10:21:31.863297 IP A.B.36.193.55024 > A.B.24.34.22: Flags [S], seq 2272566820, win 64240, options [mss 1460,sackOK,TS val 17692092 ecr 0,nop,wscale 6], length 0
10:21:31.864416 IP A.B.24.34.22 > A.B.36.193.55024: Flags [R.], seq 0, ack 2272566821, win 0, length 0
10:21:32.872586 IP A.B.36.193.55024 > A.B.24.34.22: Flags [S], seq 2272566820, win 64240, options [mss 1460,sackOK,TS val 17693102 ecr 0,nop,wscale 6], length 0
10:21:32.873247 IP A.B.24.34.22 > A.B.36.193.55024: Flags [R.], seq 0, ack 1, win 0, length 0But then the tcpdump on eno1.17:
Code:
~# tcpdump -n -i eno1.17 host A.B.24.34
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on eno1.17, link-type EN10MB (Ethernet), snapshot length 262144 bytes
10:25:18.816713 IP A.B.36.193.38426 > A.B.24.34.22: Flags [S], seq 2387003356, win 64240, options [mss 1460,sackOK,TS val 17919046 ecr 0,nop,wscale 6], length 0
10:25:19.848507 IP A.B.36.193.38426 > A.B.24.34.22: Flags [S], seq 2387003356, win 64240, options [mss 1460,sackOK,TS val 17920078 ecr 0,nop,wscale 6], length 0Only when I unchecked the firewall option and restarted the VM the TCP RST went through. brctl after the change:
Code:
~# brctl show vmbr0v17
bridge name bridge id STP enabled interfaces
vmbr0v17 8000.2cea7f9bbcb0 no eno1.17
tap510i1Is this the expected behavior or might this be a bug?

