I have been trying implement a PCI passthrough for a 25g NIC to a Windows Server 2016 guest but it does not seem to work.
The Host server is a Dell Poweredge with a 1st gen Epyc CPU. I have tried the same passthrough with CentOS 8 guests on a different server with the same hardware (same CPU same NIC) without issues.
Yet here the VMs will not boot up with the passthrough in place:
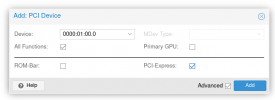
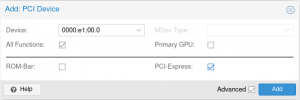
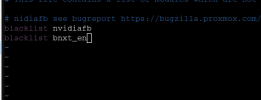
Kernel modules are loaded as described in the wiki
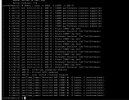
The output if
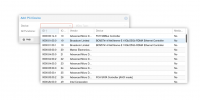
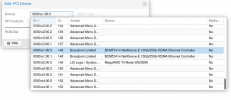
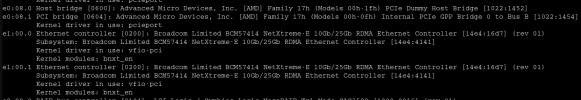
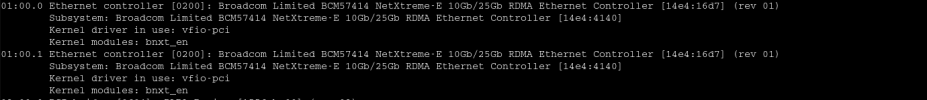
And the Correct Driver seems to be loaded:
Any ideas about what the problem is? Does maybe the a Windows guest need some additional preparation?
The Host server is a Dell Poweredge with a 1st gen Epyc CPU. I have tried the same passthrough with CentOS 8 guests on a different server with the same hardware (same CPU same NIC) without issues.
Yet here the VMs will not boot up with the passthrough in place:
TASK ERROR: start failed: command '/usr/bin/kvm -id 100 -name analsyisVM -chardev 'socket,id=qmp,path=/var/run/qemu-server/100.qmp,server,nowait' -mon 'chardev=qmp,mode=control' -chardev 'socket,id=qmp-event,path=/var/run/qmeventd.sock,reconnect=5' -mon 'chardev=qmp-event,mode=control' -pidfile /var/run/qemu-server/100.pid -daemonize -smbios 'type=1,uuid=e79e8830-310a-4c02-8588-e5dd9e48e6ef' -smp '120,sockets=1,cores=120,maxcpus=120' -nodefaults -boot 'menu=on,strict=on,reboot-timeout=1000,splash=/usr/share/qemu-server/bootsplash.jpg' -vnc unix:/var/run/qemu-server/100.vnc,password -no-hpet -cpu 'kvm64,+lahf_lm,+sep,+kvm_pv_unhalt,+kvm_pv_eoi,hv_spinlocks=0x1fff,hv_vapic,hv_time,hv_reset,hv_vpindex,hv_runtime,hv_relaxed,hv_synic,hv_stimer,hv_ipi,enforce' -m 223510 -device 'vmgenid,guid=01720a3f-afef-4d86-a0b0-c91574555808' -readconfig /usr/share/qemu-server/pve-q35-4.0.cfg -device 'usb-tablet,id=tablet,bus=ehci.0,port=1' -device 'vfio-pci,host=0000:e1:00.0,id=hostpci0.0,bus=ich9-pcie-port-1,addr=0x0.0,rombar=0,multifunction=on' -device 'vfio-pci,host=0000:e1:00.1,id=hostpci0.1,bus=ich9-pcie-port-1,addr=0x0.1' -device 'VGA,id=vga,bus=pcie.0,addr=0x1' -chardev 'socket,path=/var/run/qemu-server/100.qga,server,nowait,id=qga0' -device 'virtio-serial,id=qga0,bus=pci.0,addr=0x8' -device 'virtserialport,chardev=qga0,name=org.qemu.guest_agent.0' -device 'virtio-balloon-pci,id=balloon0,bus=pci.0,addr=0x3' -iscsi 'initiator-name=iqn.1993-08.org.debian:01:f6d9f03858f0' -drive 'file=/mnt/pve/ISOs/template/iso/virtio-win-0.1.171.iso,if=none,id=drive-ide0,media=cdrom,aio=threads' -device 'ide-cd,bus=ide.0,unit=0,drive=drive-ide0,id=ide0,bootindex=200' -device 'virtio-scsi-pci,id=scsihw0,bus=pci.0,addr=0x5' -drive 'file=/dev/zvol/Images/vm-100-disk-0,if=none,id=drive-scsi0,discard=on,format=raw,cache=none,aio=native,detect-zeroes=unmap' -device 'scsi-hd,bus=scsihw0.0,channel=0,scsi-id=0,lun=0,drive=drive-scsi0,id=scsi0,bootindex=100' -rtc 'driftfix=slew,base=localtime' -machine 'type=q35+pve1' -global 'kvm-pit.lost_tick_policy=discard'' failed: got timeout
Kernel modules are loaded as described in the wiki
The output if
dmesg | grep -e DMAR -e IOMMU -e AMD-Vi is this:
And the Correct Driver seems to be loaded:

Any ideas about what the problem is? Does maybe the a Windows guest need some additional preparation?
Last edited: