Hi,
I'm setting up a single Proxmox node with multiple Windows VMs. The physical server has multiple onboard NICs (i.e. on the motherboard).
I'd like to use ntopng to monitor all incoming/outgoing traffic from those Windows VMs.
Ideally, I'd like to run a Linux instance with ntopng on the same Proxmox node.
The two ways I can see to do this are:
For 2. I can setup mirroring on the switch - however, can I pass through that NIC directly to the ntopng Linux VM? I saw this wiki article but it's not clear if this works with on-board motherboard NICs. Also it says at top "PCI passthrough is an experimental feature in Proxmox VE" - is this still the case in late 2018?
Thanks,
Victor
I'm setting up a single Proxmox node with multiple Windows VMs. The physical server has multiple onboard NICs (i.e. on the motherboard).
I'd like to use ntopng to monitor all incoming/outgoing traffic from those Windows VMs.
Ideally, I'd like to run a Linux instance with ntopng on the same Proxmox node.
The two ways I can see to do this are:
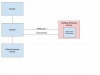
- Configure Proxmox somehow to mirror traffic within itself, and pass outgoing traffic from those Windows VMs back to another VM. Is this possible?
- Setup port mirroring on the physical switch, and plug that back into a second NIC on the server
For 2. I can setup mirroring on the switch - however, can I pass through that NIC directly to the ntopng Linux VM? I saw this wiki article but it's not clear if this works with on-board motherboard NICs. Also it says at top "PCI passthrough is an experimental feature in Proxmox VE" - is this still the case in late 2018?
Thanks,
Victor