Exactly (((
lxc machine can't get inet connection after upgrading to 6.4.4 anymore.
Would You advice how to figure out it?
Appreciate for help.
ip r
default via 10.1.1.112 dev eth0 onlink
10.1.1.0/24 dev eth0 proto kernel scope link src 10.1.1.102
pct config 102
arch: amd64
cores: 2
features: nesting=1
hostname: app
memory: 4096
nameserver: 10.1.1.112
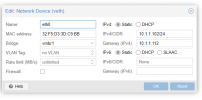
net0: name=eth0,bridge=vmbr1,gw=10.1.1.112,hwaddr=32:F5:\D3:3D:C9:BB,ip=10.1.1.102/24,type=veth
onboot: 1
ostype: debian
rootfs: local-zfs:subvol-102-disk-1,size=20G
searchdomain: domain
startup: order=2
swap: 2048
Here You are an unchangable lxc network config
lxc machine can't get inet connection after upgrading to 6.4.4 anymore.
Would You advice how to figure out it?
Appreciate for help.
ip r
default via 10.1.1.112 dev eth0 onlink
10.1.1.0/24 dev eth0 proto kernel scope link src 10.1.1.102
pct config 102
arch: amd64
cores: 2
features: nesting=1
hostname: app
memory: 4096
nameserver: 10.1.1.112
net0: name=eth0,bridge=vmbr1,gw=10.1.1.112,hwaddr=32:F5:\D3:3D:C9:BB,ip=10.1.1.102/24,type=veth
onboot: 1
ostype: debian
rootfs: local-zfs:subvol-102-disk-1,size=20G
searchdomain: domain
startup: order=2
swap: 2048
Here You are an unchangable lxc network config

Last edited:

