We added two new nodes to our cluster but are not able to migrate VMs to it as qemu appears to incorrectly indicate that the CPU doesn't support necessary 'hle' and 'rtm' features.
Error:
https://en.wikipedia.org/wiki/CPUID indicates that bit 4 relates to 'hle' and bit 11 to 'rtm':
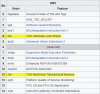
The 'rtm' CPU flag is missing and 'hle' only appears in the first core's list of support flags:
We set the guest CPU features to the lowest common CPU feature set to allow migration to any node:
We can successfully migrate the guest between other nodes, just not to the new node.
Herewith the CPU information for one of the other nodes:
PVE version information (we installed with pve-no-subscription but removed it after licensing the node):
Edit:
Downgrading to 5.3.13-2-pve makes no difference, setting CPU as 'Cascadelake-Server' or 'Skylake-Server' with a new VM yields the following error:
It only boots with CPU set as 'host' or 'kvm64'...
Edit2:
Herewith the CPU flags from one of the other cores on the new platform. 'hle' is missing on all cores besides core 1:
Regards
David Herselman
Error:
Code:
task started by HA resource agent
2020-02-14 22:19:16 starting migration of VM 374 to node 'kvm5h' (198.19.17.73)
2020-02-14 22:19:18 starting VM 374 on remote node 'kvm5h'
2020-02-14 22:19:19 [kvm5h] kvm: warning: host doesn't support requested feature: CPUID.07H:EBX.hle [bit 4]
2020-02-14 22:19:19 [kvm5h] kvm: warning: host doesn't support requested feature: CPUID.07H:EBX.rtm [bit 11]
2020-02-14 22:19:19 [kvm5h] kvm: Host doesn't support requested features
2020-02-14 22:19:20 [kvm5h] start failed: QEMU exited with code 1
2020-02-14 22:19:20 ERROR: online migrate failure - remote command failed with exit code 255
2020-02-14 22:19:20 aborting phase 2 - cleanup resources
2020-02-14 22:19:20 migrate_cancel
2020-02-14 22:19:20 ERROR: migration finished with problems (duration 00:00:05)
TASK ERROR: migration problemshttps://en.wikipedia.org/wiki/CPUID indicates that bit 4 relates to 'hle' and bit 11 to 'rtm':

The 'rtm' CPU flag is missing and 'hle' only appears in the first core's list of support flags:
Code:
processor : 0
vendor_id : GenuineIntel
cpu family : 6
model : 85
model name : Intel(R) Xeon(R) Gold 6248 CPU @ 2.50GHz
stepping : 7
microcode : 0x500002c
cpu MHz : 1672.415
cache size : 28160 KB
physical id : 0
siblings : 40
core id : 0
cpu cores : 20
apicid : 0
initial apicid : 0
fpu : yes
fpu_exception : yes
cpuid level : 22
wp : yes
flags : fpu vme de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush dts acpi mmx fxsr sse sse2 ss ht tm pbe syscall nx pdpe1gb rdtscp lm constant_tsc art arch_perfmon pebs bts rep_good nopl xtopology nonstop_tsc cpuid aperfmperf pni pclmulqdq dtes64 monitor ds_cpl vmx smx est tm2 ssse3 sdbg fma cx16 xtpr pdcm pcid dca sse4_1 sse4_2 x2apic movbe popcnt tsc_deadline_timer aes xsave avx f16c rdrand lahf_lm abm 3dnowprefetch cpuid_fault epb cat_l3 cdp_l3 invpcid_single ssbd mba ibrs ibpb stibp ibrs_enhanced tpr_shadow vnmi flexpriority ept vpid ept_ad fsgsbase tsc_adjust bmi1 hle avx2 smep bmi2 erms invpcid cqm mpx rdt_a avx512f avx512dq rdseed adx smap clflushopt clwb intel_pt avx512cd avx512bw avx512vl xsaveopt xsavec xgetbv1 xsaves cqm_llc cqm_occup_llc cqm_mbm_total cqm_mbm_local dtherm ida arat pln pts hwp hwp_act_window hwp_epp hwp_pkg_req pku ospke avx512_vnni md_clear flush_l1d arch_capabilities
bugs : spectre_v1 spectre_v2 spec_store_bypass swapgs taa itlb_multihit
bogomips : 5000.00
clflush size : 64
cache_alignment : 64
address sizes : 46 bits physical, 48 bits virtual
power management:We set the guest CPU features to the lowest common CPU feature set to allow migration to any node:
Code:
[admin@kvm5h tasks]# cat /etc/pve/nodes/kvm5b/qemu-server/374.conf
agent: 1
boot: cdn
bootdisk: scsi0
cores: 6
cpu: Broadwell
ide2: none,media=cdrom
localtime: 1
memory: 131072
name: client-sysname
net0: virtio=2F:F5:2C:2D:E5:E0,bridge=vmbr0,tag=460
numa: 1
onboot: 1
ostype: win10
protection: 1
scsi0: rbd_ssd:base-353-disk-1/vm-374-disk-0,cache=writeback,discard=on,size=100G,ssd=1
scsi1: rbd_ssd:vm-374-disk-1,cache=writeback,discard=on,size=1T,ssd=1
scsihw: virtio-scsi-pci
smbios1: uuid=d2e7fabc-e91d-468b-a430-6a7c4cc5bdba
sockets: 2
vga: cirrusWe can successfully migrate the guest between other nodes, just not to the new node.
Herewith the CPU information for one of the other nodes:
Code:
processor : 39
vendor_id : GenuineIntel
cpu family : 6
model : 79
model name : Intel(R) Xeon(R) CPU E5-2640 v4 @ 2.40GHz
stepping : 1
microcode : 0xb000038
cpu MHz : 2609.796
cache size : 25600 KB
physical id : 1
siblings : 20
core id : 12
cpu cores : 10
apicid : 57
initial apicid : 57
fpu : yes
fpu_exception : yes
cpuid level : 20
wp : yes
flags : fpu vme de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush dts acpi mmx fxsr sse sse2 ss ht tm pbe syscall nx pdpe1gb rdtscp lm constant_tsc arch_perfmon pebs bts rep_good nopl xtopology nonstop_tsc cpuid aperfmperf pni pclmulqdq dtes64 monitor ds_cpl vmx smx est tm2 ssse3 sdbg fma cx16 xtpr pdcm pcid dca sse4_1 sse4_2 x2apic movbe popcnt tsc_deadline_timer aes xsave avx f16c rdrand lahf_lm abm 3dnowprefetch cpuid_fault epb cat_l3 cdp_l3 invpcid_single pti intel_ppin ssbd ibrs ibpb stibp tpr_shadow vnmi flexpriority ept vpid ept_ad fsgsbase tsc_adjust bmi1 hle avx2 smep bmi2 erms invpcid rtm cqm rdt_a rdseed adx smap intel_pt xsaveopt cqm_llc cqm_occup_llc cqm_mbm_total cqm_mbm_local dtherm ida arat pln pts md_clear flush_l1d
bugs : cpu_meltdown spectre_v1 spectre_v2 spec_store_bypass l1tf mds swapgs taa itlb_multihit
bogomips : 4790.38
clflush size : 64
cache_alignment : 64
address sizes : 46 bits physical, 48 bits virtual
power management:PVE version information (we installed with pve-no-subscription but removed it after licensing the node):
Code:
[admin@kvm5h tasks]# pveversion -v
proxmox-ve: 6.1-2 (running kernel: 5.3.18-1-pve)
pve-manager: 6.1-7 (running version: 6.1-7/13e58d5e)
pve-kernel-5.3: 6.1-4
pve-kernel-helper: 6.1-4
pve-kernel-5.3.18-1-pve: 5.3.18-1
ceph: 14.2.6-pve1
ceph-fuse: 14.2.6-pve1
corosync: 3.0.3-pve1
criu: 3.11-3
glusterfs-client: 5.5-3
ifupdown: 0.8.35+pve1
ksm-control-daemon: 1.3-1
libjs-extjs: 6.0.1-10
libknet1: 1.14-pve1
libpve-access-control: 6.0-6
libpve-apiclient-perl: 3.0-3
libpve-common-perl: 6.0-12
libpve-guest-common-perl: 3.0-3
libpve-http-server-perl: 3.0-4
libpve-storage-perl: 6.1-4
libqb0: 1.0.5-1
libspice-server1: 0.14.2-4~pve6+1
lvm2: 2.03.02-pve4
lxc-pve: 3.2.1-1
lxcfs: 3.0.3-pve60
novnc-pve: 1.1.0-1
openvswitch-switch: 2.10.0+2018.08.28+git.8ca7c82b7d+ds1-12+deb10u1
proxmox-mini-journalreader: 1.1-1
proxmox-widget-toolkit: 2.1-3
pve-cluster: 6.1-4
pve-container: 3.0-19
pve-docs: 6.1-4
pve-edk2-firmware: 2.20191127-1
pve-firewall: 4.0-10
pve-firmware: 3.0-5
pve-ha-manager: 3.0-8
pve-i18n: 2.0-4
pve-qemu-kvm: 4.1.1-2
pve-xtermjs: 4.3.0-1
qemu-server: 6.1-5
smartmontools: 7.1-pve2
spiceterm: 3.1-1
vncterm: 1.6-1
zfsutils-linux: 0.8.3-pve1Edit:
Downgrading to 5.3.13-2-pve makes no difference, setting CPU as 'Cascadelake-Server' or 'Skylake-Server' with a new VM yields the following error:
Code:
/dev/rbd0
kvm: warning: host doesn't support requested feature: CPUID.07H:EBX.hle [bit 4]
kvm: warning: host doesn't support requested feature: CPUID.07H:EBX.rtm [bit 11]
kvm: Host doesn't support requested features
TASK ERROR: start failed: QEMU exited with code 1It only boots with CPU set as 'host' or 'kvm64'...
Edit2:
Herewith the CPU flags from one of the other cores on the new platform. 'hle' is missing on all cores besides core 1:
Code:
processor : 79
vendor_id : GenuineIntel
cpu family : 6
model : 85
model name : Intel(R) Xeon(R) Gold 6248 CPU @ 2.50GHz
stepping : 7
microcode : 0x500002c
cpu MHz : 2160.858
cache size : 28160 KB
physical id : 1
siblings : 40
core id : 28
cpu cores : 20
apicid : 121
initial apicid : 121
fpu : yes
fpu_exception : yes
cpuid level : 22
wp : yes
flags : fpu vme de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush dts acpi mmx fxsr sse sse2 ss ht tm pbe syscall nx pdpe1gb rdtscp lm constant_tsc art arch_perfmon pebs bts rep_good nopl xtopology nonstop_tsc cpuid aperfmperf pni pclmulqdq dtes64 monitor ds_cpl vmx smx est tm2 ssse3 sdbg fma cx16 xtpr pdcm pcid dca sse4_1 sse4_2 x2apic movbe popcnt tsc_deadline_timer aes xsave avx f16c rdrand lahf_lm abm 3dnowprefetch cpuid_fault epb cat_l3 cdp_l3 invpcid_single ssbd mba ibrs ibpb stibp ibrs_enhanced tpr_shadow vnmi flexpriority ept vpid ept_ad fsgsbase tsc_adjust bmi1 avx2 smep bmi2 erms invpcid cqm mpx rdt_a avx512f avx512dq rdseed adx smap clflushopt clwb intel_pt avx512cd avx512bw avx512vl xsaveopt xsavec xgetbv1 xsaves cqm_llc cqm_occup_llc cqm_mbm_total cqm_mbm_local dtherm ida arat pln pts hwp hwp_act_window hwp_epp hwp_pkg_req pku ospke avx512_vnni md_clear flush_l1d arch_capabilities
bugs : spectre_v1 spectre_v2 spec_store_bypass swapgs taa itlb_multihit
bogomips : 5001.73
clflush size : 64
cache_alignment : 64
address sizes : 46 bits physical, 48 bits virtual
power management:Regards
David Herselman
Last edited:

