I wanted to post a reply because there wasn't info on the web for MY search and I want to make sure someone else can find it. You always have to ask the RIGHT questions, don't you?
I was/am trying to get tailscale setup on an Ubuntu Server 22.04 - tailscaled.service was failing because /dev/net/tun wasn't present... so I went searching for tailscale, tailscaled.service, /dev/net/tun fails, etc etc etc. The correct question would have been Tailscaled.service fails on a Proxmox LXC container.

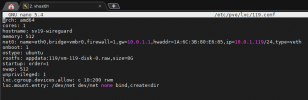
Last, the solution above that worked for me was adding the TWO lines of text to xxx.conf in the /etc/pve/lxc directory on my PVE system... the two lines were:
```
lxc.cgroup.devices.allow: c 10:200 rwm
lxc.mount.entry: /dev/net dev/net none bind,create=dir
```
Once added to my xxx.conf file, and the lxc container rebooted, /dev/net/tun was present - tailscale installed and went up perfectly.
Hope this helps someone else searching in the future.