Hi There,
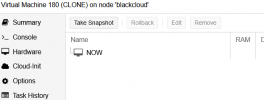
When I try to clone an existing VM from the (not-current/not-latest) snapshot, I get the following error (with the error seemingly randomly either related to scsi0 or efidisk0)? Is this expected or a bug?
The configuration of the source VM being cloned is as follows:
Thanks!
When I try to clone an existing VM from the (not-current/not-latest) snapshot, I get the following error (with the error seemingly randomly either related to scsi0 or efidisk0)? Is this expected or a bug?
The configuration of the source VM being cloned is as follows:
Code:
root@pve-host1:~# cat /etc/pve/qemu-server/111.conf
agent: 1
bios: ovmf
boot: cdn
bootdisk: scsi0
cores: 4
cpu: host
efidisk0: local-zfs:vm-111-disk-1,size=1M
ide2: none,media=cdrom
memory: 8192
name: pve-vm-docker-1
net0: virtio=<MAC>,bridge=vmbr0,firewall=1
numa: 0
onboot: 1
ostype: l26
parent: Snapshot3
scsi0: local-zfs:vm-111-disk-0,discard=on,size=20G,ssd=1
scsihw: virtio-scsi-pci
smbios1: uuid=<ID>
sockets: 1
vga: virtio
vmgenid: <ID>
[Snapshot1]
#Initial Install, set timezone, apt update, install qemu-guest-agent, install nfs-common, create NFS mounts, update /etc/fstab, extend root volume to 100%.
agent: 1
bios: ovmf
bootdisk: scsi0
cores: 4
cpu: host
efidisk0: local-zfs:vm-111-disk-1,size=1M
ide2: none,media=cdrom
memory: 8192
name: pve-vm-docker-ceph-1
net0: virtio=<MAC>,bridge=vmbr0,firewall=1
numa: 0
ostype: l26
scsi0: local-zfs:vm-111-disk-0,discard=on,size=20G,ssd=1
scsihw: virtio-scsi-pci
smbios1: uuid=<ID>
snaptime: 1586835511
sockets: 1
vga: virtio
vmgenid: <ID>
[Snapshot2]
#Before reinstall to Ubuntu 20.04 LTS
agent: 1
bios: ovmf
bootdisk: scsi0
cores: 4
cpu: host
efidisk0: local-zfs:vm-111-disk-1,size=1M
ide2: none,media=cdrom
memory: 8192
name: pve-vm-docker-1
net0: virtio=<MAC>,bridge=vmbr0,firewall=1
numa: 0
onboot: 1
ostype: l26
parent: Snapshot1
scsi0: local-zfs:vm-111-disk-0,discard=on,size=20G,ssd=1
scsihw: virtio-scsi-pci
smbios1: uuid=<ID>
snaptime: 1592295156
sockets: 1
vga: virtio
vmgenid: <ID>
[Snapshot3]
#Ubuntu 20.04 LTS%3A Initial Install, set timezone, apt update, install qemu-guest-agent, install nfs-common, create NFS / gluster mounts, update /etc/hosts, update /etc/fstab, install gluster-client
agent: 1
bios: ovmf
boot: dcn
bootdisk: scsi0
cores: 4
cpu: host
efidisk0: local-zfs:vm-111-disk-1,size=1M
ide2: none,media=cdrom
memory: 8192
name: pve-vm-docker-1
net0: virtio=<MAC>,bridge=vmbr0,firewall=1
numa: 0
onboot: 1
ostype: l26
parent: Snapshot2
scsi0: local-zfs:vm-111-disk-0,discard=on,size=20G,ssd=1
scsihw: virtio-scsi-pci
smbios1: uuid=<ID>
snaptime: 1592298157
sockets: 1
vga: virtio
vmgenid: <ID>Thanks!