Hello,
I want to create a new user that is able to create VMs by itself, but without seeing other VMs on the node. I've been playing with permissions in the last hours but unfortunately I can't find out what's the issue.
As a last solution, for testing purposes, I've added
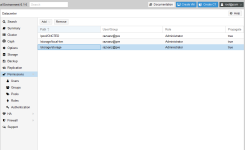
At this point the user has:
Any hints why this is not working? Any way to see the logs?
Thank you!
I want to create a new user that is able to create VMs by itself, but without seeing other VMs on the node. I've been playing with permissions in the last hours but unfortunately I can't find out what's the issue.
As a last solution, for testing purposes, I've added
Administrator privileges to the user. Even so, the user gets this error, every time he tries to click Finish.
Code:
Permission check failed (403)At this point the user has:
Administrator@Pool->PermissionsAdministrator@local-lvmAdministrator@storage(CIFS mount for ISO and backups)- The
Poolhaslocal-lvmandstorage@Members

Any hints why this is not working? Any way to see the logs?
Thank you!