Our servers are currently under a spam attack trying to use our mail gateways as open relay and for reasons yet unknown, quite a few got through.
After a reboot (and update) the vast majority of connection requests get blocked with a relay access denied, as they should. But there are some which still get accepted and would be passed on if not for an additional rule I added today.
The screenshot below shows two emails from attacker to a random email address, none of the domains are ours.
The first one is only caught because of the Block DHL rule I created as a workaround
The second one is rejected right away, as it should but it's unclear why.
Can anyone spot a difference between those two emails or can think of a reason why the first one is accepted initially?
The actual sender or receiver email doesn't seem to matter, so there must be something else at play?
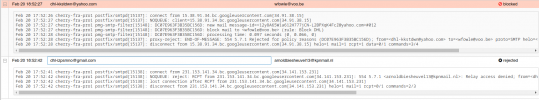
After a reboot (and update) the vast majority of connection requests get blocked with a relay access denied, as they should. But there are some which still get accepted and would be passed on if not for an additional rule I added today.
The screenshot below shows two emails from attacker to a random email address, none of the domains are ours.
The first one is only caught because of the Block DHL rule I created as a workaround
The second one is rejected right away, as it should but it's unclear why.
Can anyone spot a difference between those two emails or can think of a reason why the first one is accepted initially?
The actual sender or receiver email doesn't seem to matter, so there must be something else at play?


