Hi all,
I am having issues passing through a SAS2008 LSI card to a TrueNAS VM in Proxmox.
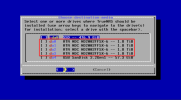
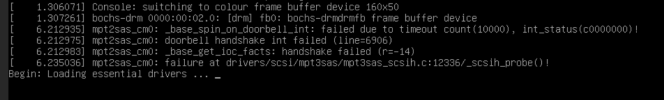
The installer works no problem running TrueNAS on bare-metal but when I run the TrueNAS installer in a VM with the HBA card passed through, the machine hangs on the following screen:
Obviously it doesn't hang on baremetal so I think I am missing something somewhere?
Hardware:
HP Proliant ML310e Gen8 V2
Xeon CPU E3-1245 v3
32GB DDR3 ECC Memory
This is my GRUB commandline:
My VM config:
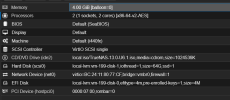
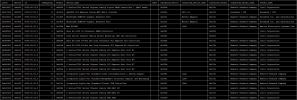
IOMMU groups are separated OK:
Any help is appreciated
I am having issues passing through a SAS2008 LSI card to a TrueNAS VM in Proxmox.
The installer works no problem running TrueNAS on bare-metal but when I run the TrueNAS installer in a VM with the HBA card passed through, the machine hangs on the following screen:

Obviously it doesn't hang on baremetal so I think I am missing something somewhere?
Hardware:
HP Proliant ML310e Gen8 V2
Xeon CPU E3-1245 v3
32GB DDR3 ECC Memory
This is my GRUB commandline:
Code:
GRUB_CMDLINE_LINUX_DEFAULT="quiet intel_iommu=on,relax_rmrr allow_unsafe_interrupts=1 pcie_acs_override=downstream,multifunction"My VM config:

IOMMU groups are separated OK:

Any help is appreciated