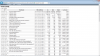
I'm a ProxMox user with a ProxMox server with the following configuration: Intel i7 ,24 GB, Hard disk 2 TB, 1 primary ip address, and 4 ip fail over.
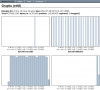
Somebody is attacking one of the ip fail over, saturating all the bandwith of the server network interface. My provider says that it can't do nothing without logs, and it advice to use a firewall... I use ZeroShell firewall on the attacked ip fail over but I don't know to log these attacks...
Unfortunately, although I have a firewall , it does not solve the problem because the saturation of bandwith it can't be solved from firewall: my provider says that the one solution is to DISABLE THE IP DURING THE ATTACK, but it means that I have to put off the mail server, the voip server, and the web server!!!
Is it possibile to log all the traffic , mac address, ip address , etc... of the attacked ip interface?
To enable the attacked ip interface, I use this command:
ip route add IP.FAIL.OVER dev vmbr1
To disable the attacked ip interface, I use this command:
ip route del IP.FAIL.OVER dev vmbr1
I hope that somebody can help me...
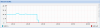
Somebody is attacking one of the ip fail over, saturating all the bandwith of the server network interface. My provider says that it can't do nothing without logs, and it advice to use a firewall... I use ZeroShell firewall on the attacked ip fail over but I don't know to log these attacks...
Unfortunately, although I have a firewall , it does not solve the problem because the saturation of bandwith it can't be solved from firewall: my provider says that the one solution is to DISABLE THE IP DURING THE ATTACK, but it means that I have to put off the mail server, the voip server, and the web server!!!
Is it possibile to log all the traffic , mac address, ip address , etc... of the attacked ip interface?
To enable the attacked ip interface, I use this command:
ip route add IP.FAIL.OVER dev vmbr1
To disable the attacked ip interface, I use this command:
ip route del IP.FAIL.OVER dev vmbr1
I hope that somebody can help me...
Last edited: