Hi,
I have the following challenge.
If I show the active session with this command "iscsiadm --mode session --print=1"
During regular operations my iSCSI connection looks like this.

When a port reinitialize is done by the target I have this state.
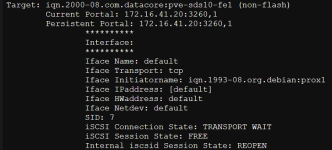
I have already made the following changes in iscsid.conf
node.startup = automatic
node.leading_login = Yes
node.session.timeo.replacement_timeout = 15
I had already tried the commands
iscsiadm -m node --op=update -n node.conn[0].startup -v automatic
iscsiadm -m node --op=update -n node.startup -v automatic
The solution is to provied a logout and login of the port or the tough method to restart iscsid
Can anyone tell me how I can solve this without manual intervention?
I am grateful for any solutions.
Regards
Rainer
I have the following challenge.
If I show the active session with this command "iscsiadm --mode session --print=1"
During regular operations my iSCSI connection looks like this.

When a port reinitialize is done by the target I have this state.

I have already made the following changes in iscsid.conf
node.startup = automatic
node.leading_login = Yes
node.session.timeo.replacement_timeout = 15
I had already tried the commands
iscsiadm -m node --op=update -n node.conn[0].startup -v automatic
iscsiadm -m node --op=update -n node.startup -v automatic
The solution is to provied a logout and login of the port or the tough method to restart iscsid
Can anyone tell me how I can solve this without manual intervention?
I am grateful for any solutions.
Regards
Rainer

